As an Ethical Hacker, you have been asked to test an application’s vulnerability to SQL injection. During testing, you discover an entry field that appears susceptible. However, the backend database is unknown, and regular SQL injection techniques have failed to produce useful information. Which advanced SQL injection technique should you apply next?
Which address translation scheme would allow a single public IP address to always correspond to a single machine on an internal network, allowing "server publishing"?
During a UDP service enumeration scan, the tester sees that some ports respond with ICMP Type 3 Code 3 (Port Unreachable), while most remain silent. No firewall or IDS is interfering. What can the tester conclude about the non-responsive ports?
You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?
ping - * 6 192.168.0.101
Output:
Pinging 192.168.0.101 with 32 bytes of data:
Reply from 192.168.0.101: bytes=32 time<1ms TTL=128
...
Packets: Sent = 6, Received = 6, Lost = 0 (0% loss)
What does the option * indicate?
A tester evaluates a login form that builds SQL queries using unsanitized input. By submitting a single quote ('), the tester bypasses authentication and logs in. What type of SQL injection occurred?
Josh has finished scanning a network and has discovered multiple vulnerable services. He knows that several of these usually have protections against external sources but are frequently susceptible to internal users. He decides to draft an email, spoof the sender as the internal IT team, and attach a malicious file disguised as a financial spreadsheet. Before Josh sends the email, he decides to investigate other methods of getting the file onto the system. For this particular attempt, what was the last stage of the cyber kill chain that Josh performed?
While assessing a web server, a tester sends malformed HTTP requests and compares responses to identify the server type and version. What technique is being employed?
Garry is a network administrator in an organization. He uses SNMP to manage networked devices from a remote location. To manage nodes in the network, he uses MIB. which contains formal descriptions of all network objects managed by SNMP. He accesses the contents of MIB by using a web browser either by entering the IP address and Lseries.mlb or by entering the DNS library name and Lseries.mlb. He is currently retrieving information from an MIB that contains object types for workstations and server services. Which of the following types of MIB is accessed by Garry in the above scenario?
A cyber attacker has initiated a series of activities against a high-profile organization following the Cyber Kill
Chain Methodology. The attacker is presently in the “Delivery” stage. As an Ethical Hacker, you are trying to
anticipate the adversary's next move. What is the most probable subsequent action from the attacker based on
the Cyber Kill Chain Methodology?
Jason, an attacker, targeted an organization to perform an attack on its Internet-facing web server with the intention of gaining access to backend servers, which are protected by a firewall. In this process, he used a URL https://xyz.com/feed.php?url:externaIsile.com/feed/to to obtain a remote feed and altered the URL input to the local host to view all the local resources on the target server. What is the type of attack Jason performed In the above scenario?
A pen tester is configuring a Windows laptop for a test. In setting up Wireshark, what driver and library are required to allow the NIC to work in promiscuous mode?
A university's online registration system is disrupted by a combined DNS reflection and HTTP Slowloris DDoS attack. Standard firewalls cannot mitigate the attack without blocking legitimate users. What is the best mitigation strategy?
While browsing his Facebook feed, Matt sees a picture one of his friends posted with the caption, "Learn more about your friends!", along with a number of personal questions. Matt is suspicious and texts his friend, who confirms that he did indeed post it. With assurance that the post is legitimate, Matt responds to the questions in the post. A few days later, Matt's bank account has been accessed, and the password has been changed. What most likely happened?
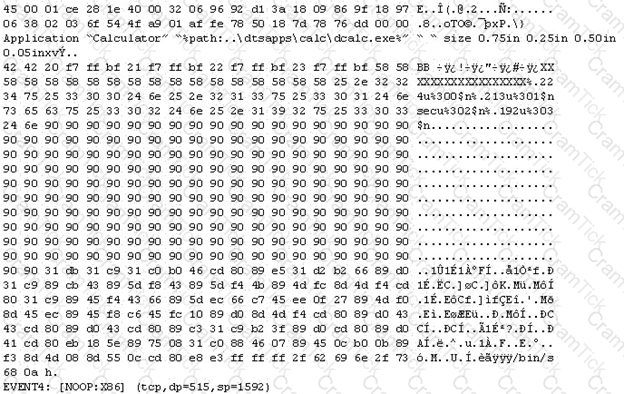
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry.
You notice the value 0x90, which is the most common NOOP instruction for the Intel processor.
You also notice "/bin/sh" in the ASCII part of the output.
As an analyst, what would you conclude about the attack?
While testing a web application in development, you notice that the web server does not properly ignore the “dot dot slash” (../) character string and instead returns the file listing of a folder structure of the server.
What kind of attack is possible in this scenario?
Which regulation defines security and privacy controls for Federal information systems and organizations?
A future-focused security audit discusses risks where attackers collect encrypted data today, anticipating they will be able to decrypt it later using quantum computers. What is this threat commonly known as?
You are performing a penetration test for a client and have gained shell access to a Windows machine on the internal network. You intend to retrieve all DNS records for the internal domain. If the DNS server is at 192.168.10.2 and the domain name is abccorp.local, what command would you type at the nslookup prompt to attempt a zone transfer?
Which type of security feature stops vehicles from crashing through the doors of a building?
Nicolas just found a vulnerability on a public-facing system that is considered a zero-day vulnerability. He sent an email to the owner of the public system describing the problem and how the owner can protect themselves from that vulnerability. He also sent an email to Microsoft informing them of the problem that their systems are exposed to. What type of hacker is Nicolas?
Customer data in a cloud environment was exposed due to an unknown vulnerability. What is the most likely cause?
Which social engineering attack involves impersonating a co-worker or authority figure to extract confidential information?
A penetration tester is evaluating the security of a mobile application and discovers that it lacks proper input validation. The tester suspects that the application is vulnerable to a malicious code injection attack. What is the most effective way to confirm and exploit this vulnerability?
Which of the following statements is FALSE with respect to Intrusion Detection Systems?
A multinational corporation recently survived a severe Distributed Denial-of-Service (DDoS) attack and has implemented enhanced security measures. During an audit, you discover that the organization uses both hardware- and cloud-based solutions to distribute incoming traffic in order to absorb and mitigate DDoS attacks while ensuring legitimate traffic remains available. What type of DDoS mitigation strategy is the company utilizing?
Steven connected his iPhone to a public computer that had been infected by Clark, an attacker. After establishing the connection with the public computer, Steven enabled iTunes WI-FI sync on the computer so that the device could continue communication with that computer even after being physically disconnected. Now, Clark gains access to Steven’s iPhone through the infected computer and is able to monitor and read all of Steven’s activity on the iPhone, even after the device is out of the communication zone.
Which of the following attacks is performed by Clark in above scenario?
Harper, a software engineer, is developing an email application. To ensure the confidentiality of email messages, Harper uses a symmetric-key block cipher having a classical 12- or 16-round Feistel network with a block size of 64 bits for encryption, which includes large 8 x 32-bit S-boxes (S1, S2, S3, S4) based on bent functions, modular addition and subtraction, key-dependent rotation, and XOR operations. This cipher also uses a masking key (Km1) and a rotation key (Kr1) for performing its functions.
What is the algorithm employed by Harper to secure the email messages?
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple, small sized packets to the target computer, making it very difficult for an IDS to detect the attack signatures. Which tool can be used to perform session splicing attacks?
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host
10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he
applied his ACL configuration in the router, nobody can access the ftp, and the permitted hosts cannot access
the Internet. According to the next configuration, what is happening in the network?
access-list 102 deny tcp any any
access-list 104 permit udp host 10.0.0.3 any
access-list 110 permit tcp host 10.0.0.2 eq www any
access-list 108 permit tcp any eq ftp any
Attackers persisted by modifying legitimate system utilities and services. What key step helps prevent similar threats?
You detect the presence of a kernel-level rootkit embedded deeply within an operating system. Given the critical nature of the infection, which remediation strategy should be followed to effectively remove the rootkit while minimizing long-term risk?
Which results will be returned with the following Google search query?
site:target.com –site:Marketing.target.com accounting
Which type of attack attempts to overflow the content-addressable memory (CAM) table in an Ethernet switch?
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days, Bab denies that he had ever sent a mail. What do you want to ““know”” to prove yourself that it was Bob who had send a mail?
You are an ethical hacker contracted to conduct a security audit for a company. During the audit, you discover that the company's wireless network is using WEP encryption. You understand the vulnerabilities associated with WEP and plan to recommend a more secure encryption method. Which of the following would you recommend as a Suitable replacement to enhance the security of the company's wireless network?
A user on your Windows 2000 network has discovered that he can use L0phtCrack to sniff the SMB exchanges which carry user logons. The user is plugged into a hub with 23 other systems.
However, he is unable to capture any logons though he knows that other users are logging in.
What do you think is the most likely reason behind this?
Clark is a professional hacker. He created and configured multiple domains pointing to the same host to switch quickly between the domains and avoid detection.
Identify the behavior of the adversary In the above scenario.
Which action would most effectively increase the security of a virtual-hosted web server?
During testing against a network protected by a signature-based IDS, the tester notices that standard scans are blocked. To evade detection, the tester sends TCP headers split into multiple small IP fragments so the IDS cannot reassemble or interpret them, but the destination host can. What technique is being used?
An experienced cyber attacker has created a fake Linkedin profile, successfully impersonating a high-ranking official from a well-established company, to execute a social engineering attack. The attacker then connected with other employees within the organization, receiving invitations to exclusive corporate events and gaining
access to proprietary project details shared within the network. What advanced social engineering technique has the attacker primarily used to exploit the system and what is the most likely immediate threat to the organization?
During an internal assessment, a penetration tester gains access to a hash dump containing NTLM password hashes from a compromised Windows system. To crack the passwords efficiently, the tester uses a high-performance CPU setup with Hashcat, attempting millions of password combinations per second. Which technique is being optimized in this scenario?
CyberTech Inc. recently experienced SQL injection attacks on its official website. The company appointed Bob, a security professional, to build and incorporate defensive strategies against such attacks. Bob adopted a practice whereby only a list of entities such as the data type, range, size, and value, which have been approved for secured access, is accepted. What is the defensive technique employed by Bob in the above scenario?
Eric has discovered a fantastic package of tools named Dsniff on the Internet. He has learnt to use these tools in his lab and is now ready for real world exploitation. He was able to effectively intercept communications between the two entities and establish credentials with both sides of the connections. The two remote ends of the communication never notice that Eric is relaying the information between the two. What would you call this attack?
Sam, a web developer, was instructed to incorporate a hybrid encryption software program into a web application to secure email messages. Sam used an encryption software, which is a free implementation of the OpenPGP standard that uses both symmetric-key cryptography and asymmetric-key cryptography for improved speed and secure key exchange. What is the encryption software employed by Sam for securing the email messages?
jane invites her friends Alice and John over for a LAN party. Alice and John access Jane's wireless network without a password. However. Jane has a long, complex password on her router. What attack has likely occurred?
Bill is a network administrator. He wants to eliminate unencrypted traffic inside his company's network. He decides to setup a SPAN port and capture all traffic to the datacenter. He immediately discovers unencrypted traffic in port UDP 161. what protocol is this port using and how can he secure that traffic?
Suppose that you test an application for the SQL injection vulnerability. You know that the backend database is based on Microsoft SQL Server. In the login/password form, you enter the following credentials:
Username: attack' or 1=1 --
Password: 123456
Based on the above credentials, which of the following SQL commands are you expecting to be executed by the server, if there is indeed an SQL injection vulnerability?
An employee finds a USB drive labeled “Employee Salary Info 2024” and plugs it into a company computer, causing erratic behavior. What type of social engineering attack is this?
When considering how an attacker may exploit a web server, what is web server footprinting?
You have compromised a server on a network and successfully opened a shell. You aimed to identify all operating systems running on the network. However, as you attempt to fingerprint all machines in the network using the nmap syntax below, it is not going through.
invictus@victim_server:~$ nmap -T4 -O 10.10.0.0/24
TCP/IP fingerprinting (for OS scan) xxxxxxx xxxxxx xxxxxxxxx. QUITTING!
What seems to be wrong?
You just set up a security system in your network. In what kind of system would you find the following string of characters used as a rule within its configuration?
alert tcp any any -> 192.168.100.0/24 21 (msg: “FTP on the network!”;)
A financial institution's online banking platform is experiencing intermittent downtime caused by a sophisticated DDoS attack that combines SYN floods and HTTP GET floods from a distributed botnet. Standard firewalls and load balancers cannot mitigate the attack without affecting legitimate users. To protect their infrastructure and maintain service availability, which advanced mitigation strategy should the institution implement?
A penetration tester is assessing an IoT thermostat used in a smart home system. The device communicates with a cloud server for updates and commands. The tester discovers that communication between the device and the cloud server is not encrypted. What is the most effective way to exploit this vulnerability?
Which method best bypasses client-side controls without triggering server-side alarms?
Attacker Rony Installed a rogue access point within an organization's perimeter and attempted to Intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by Johnson in the above scenario?
Firewalls are the software or hardware systems that are able to control and monitor the traffic coming in and out the target network based on pre-defined set of rules. Which of the following types of firewalls can protect against SQL injection attacks?
An attacker exploits legacy protocols to perform advanced sniffing. Which technique is the most difficult to detect and neutralize?
Fleet vehicles with smart locking systems were compromised after attackers captured unique signals from key fobs. What should the security team prioritize to confirm and prevent this attack?
Which of the following incident handling process phases is responsible for defining rules, collaborating human workforce, creating a back-up plan, and testing the plans for an organization?
While conducting a covert penetration test on a UNIX-based infrastructure, the tester decides to bypass intrusion detection systems by sending specially crafted TCP packets with an unusual set of flags enabled. These packets do not initiate or complete any TCP handshake. During the scan, the tester notices that when certain ports are probed, there is no response from the target, but for others, a TCP RST (reset) packet is received. The tester notes that this behavior consistently aligns with open and closed ports. Based on these observations, which scanning technique is most likely being used?
A senior executive receives a personalized email with the subject line “Annual Performance Review 2024.” The email contains a downloadable PDF that installs a backdoor when opened. The email appears to come from the CEO and includes company branding. Which phishing method does this best illustrate?
Your network infrastructure is under a SYN flood attack. The attacker has crafted an automated botnet to
simultaneously send 's' SYN packets per second to the server. You have put measures in place to manage ‘f
SYN packets per second, and the system is designed to deal with this number without any performance issues.
If 's' exceeds ‘f', the network infrastructure begins to show signs of overload. The system's response time
increases exponentially (24k), where 'k' represents each additional SYN packet above the ff limit. Now, considering 's=500' and different 'f values, in which scenario is the server most likely to experience overload and significantly increased response times?
Take a look at the following attack on a Web Server using obstructed URL:
Take a look at the following attack on a Web Server using an obfuscated URL:
How would you protect from these attacks?
You suspect a Man-in-the-Middle (MitM) attack inside the network. Which network activity would help confirm this?
A penetration tester suspects that a web application's login form is vulnerable to SQL injection due to improper sanitization of user input. What is the most appropriate approach to test for SQL injection in the login form?
A penetration tester is assessing a web application that does not properly sanitize user input in the search field. The tester suspects the application is vulnerable to a SQL injection attack. Which approach should the tester take to confirm the vulnerability?
A penetration tester discovers malware on a system that disguises itself as legitimate software but performs malicious actions in the background. What type of malware is this?
BitLocker encryption has been implemented for all the Windows-based computers in an organization. You are concerned that someone might lose their cryptographic key. Therefore, a mechanism was implemented to recover the keys from Active Directory.
What is this mechanism called in cryptography?
A large e-commerce organization is planning to implement a vulnerability assessment solution to enhance its security posture. They require a solution that imitates the outside view of attackers, performs well-organized inference-based testing, scans automatically against continuously updated databases, and supports multiple networks. Given these requirements, which type of vulnerability assessment solution would be most appropriate?
Sam, a professional hacker. targeted an organization with intention of compromising AWS IAM credentials. He attempted to lure one of the employees of the organization by initiating fake calls while posing as a legitimate employee. Moreover, he sent phishing emails to steal the AWS 1AM credentials and further compromise the employee's account. What is the technique used by Sam to compromise the AWS IAM credentials?
Ralph, a professional hacker, targeted Jane, who had recently bought new systems for her company. After a few days, Ralph contacted Jane while masquerading as a legitimate customer support executive, informing that her systems need to be serviced for proper functioning and that customer support will send a computer technician. Jane promptly replied positively. Ralph entered Jane's company using this opportunity and gathered sensitive information by scanning terminals for passwords, searching for important documents in desks, and rummaging bins. What is the type of attack technique Ralph used on jane?
After a breach, investigators discover attackers used modified legitimate system utilities and a Windows service to persist undetected and harvest credentials. What key step would best protect against similar future attacks?
A penetration tester is assessing a company's executive team for vulnerability to sophisticated social engineering attacks by impersonating a trusted vendor and leveraging internal communications. What is the most effective social engineering technique to obtain sensitive executive credentials without being detected?
During a red team test, a web application dynamically builds SQL queries using a numeric URL parameter. The tester sends the following request:
http://vulnerableapp.local/view.php?id=1; DROP TABLE users;
The application throws errors and the users table is deleted. Which SQL injection technique was used?
The network in ABC company is using the network address 192.168.1.64 with mask 255.255.255.192. In the network the servers are in the addresses 192.168.1.122, 192.168.1.123 and 192.168.1.124. An attacker is trying to find those servers but he cannot see them in his scanning. The command he is using is: nmap 192.168.1.64/28.
Why he cannot see the servers?
An IoT traffic light shows anomalous traffic to an external IP and has an open port. What should be your next step?
Ben purchased a new smartphone and received some updates on it through the OTA method. He received two messages: one with a PIN from the network operator and another asking him to enter the PIN received from the operator. As soon as he entered the PIN, the smartphone started functioning in an abnormal manner.
What is the type of attack performed on Ben in the above scenario?
You are a security officer of a company. You had an alert from IDS that indicates that one PC on your Intranet is connected to a blacklisted IP address (C2 Server) on the Internet. The IP address was blacklisted just before the alert. You are starting an investigation to roughly analyze the severity of the situation. Which of the following is appropriate to analyze?
Chandler works as a pen-tester in an IT firm in New York. As part of detecting viruses in the systems, he uses a detection method where the antivirus executes the malicious code on a virtual machine to simulate CPU and memory activities.
Which type of virus detection method did Chandler use in this context?
An attacker decided to crack the passwords used by industrial control systems. In this process, he employed a loop strategy to recover these passwords. He used one character at a time to check whether the first character entered is correct; if so, he continued the loop for consecutive characters. If not, he terminated the loop. Furthermore, the attacker checked how much time the device took to finish one complete password authentication process, through which he deduced how many characters entered are correct.
What is the attack technique employed by the attacker to crack the passwords of the industrial control systems?
You are a security analyst conducting a footprinting exercise for a new client to gather information without direct interaction. After using search engines and public databases, you consider using Google Hacking (Google Dorking) techniques to uncover further vulnerabilities. Which option best justifies this decision?
What is the following command used for?
sqlmap.py -u "http://10.10.1.20/?p=1 &forumaction=search" -dbs
Alice, a professional hacker, targeted an organization's cloud services. She infiltrated the targets MSP provider by sending spear-phishing emails and distributed custom-made malware to compromise user accounts and gain remote access to the cloud service. Further, she accessed the target customer profiles with her MSP account, compressed the customer data, and stored them in the MSP. Then, she used this information to launch further attacks on the target organization. Which of the following cloud attacks did Alice perform in the above scenario?
Suppose your company has just passed a security risk assessment exercise. The results display that the risk of the breach in the main company application is 50%. Security staff has taken some measures and
implemented the necessary controls. After that, another security risk assessment was performed showing that risk has decreased to 10%. The risk threshold for the application is 20%. Which of the following risk decisions will be the best for the project in terms of its successful continuation with the most business profit?
Joel, a professional hacker, targeted a company and identified the types of websites frequently visited by its employees. Using this information, he searched for possible loopholes in these websites and injected a malicious script that can redirect users from the web page and download malware onto a victim's machine. Joel waits for the victim to access the infected web application so as to compromise the victim's machine. Which of the following techniques is used by Joel in the above scenario?
If a token and 4-digit personal identification number (PIN) are used to access a computer system and the token performs off-line checking for the correct PIN, what type of attack is possible?
A security analyst is investigating a potential network-level session hijacking incident. During the investigation, the analyst finds that the attacker has been using a technique in which they injected an authentic-looking reset packet using a spoofed source IP address and a guessed acknowledgment number. As a result, the victim's connection was reset. Which of the following hijacking techniques has the attacker most likely used?
Abnormal DNS resolution behavior is detected on an internal network. Users are redirected to altered login pages. DNS replies come from an unauthorized internal IP and are faster than legitimate responses. ARP spoofing alerts are also detected. What sniffing-based attack is most likely occurring?
During a physical penetration test simulating a social engineering attack, a threat actor walks into the lobby of a target organization dressed as a field technician from a known external vendor. Carrying a fake ID badge and referencing a known company name, the attacker confidently claims they’ve been dispatched to perform a routine server room upgrade. Using internal-sounding terminology and referencing real employee names gathered via OSINT, the individual conveys urgency. The receptionist, recognizing the vendor name and the convincing language, allows access without verifying the credentials.
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and keyloggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients’ hosts and servers?
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
A penetration tester is assessing a web application that uses dynamic SQL queries for searching users in the database. The tester suspects the search input field is vulnerable to SQL injection. What is the best approach to confirm this vulnerability?
A penetration tester evaluates an industrial control system (ICS) that manages critical infrastructure. The tester discovers that the system uses weak default passwords for remote access. What is the most effective method to exploit this vulnerability?
Matthew, a black hat, has managed to open a meterpreter session to one of the kiosk machines in Evil Corp’s lobby. He checks his current SID, which is:
S-1-5-21-1223352397-1872883824-861252104-501
What needs to happen before Matthew has full administrator access?
A penetration tester is tasked with assessing the security of an Android mobile application that stores sensitive user data. The tester finds that the application does not use proper encryption to secure data at rest. What is the most effective way to exploit this vulnerability?
During a cloud security assessment, you discover a former employee still has access to critical cloud resources months after leaving. Which practice would most effectively prevent this?
An attacker redirects the victim to malicious websites by sending them a malicious link by email. The link appears authentic but redirects the victim to a malicious web page, which allows the attacker to steal the victim's data. What type of attack is this?
A penetration tester discovers that a web application uses unsanitized user input to dynamically generate file paths. The tester identifies that the application is vulnerable to Remote File Inclusion (RFI). Which action should the tester take to exploit this vulnerability?
What information security law or standard aims at protecting stakeholders and the general public from accounting errors and fraudulent activities within organizations?
Peter, a system administrator working at a reputed IT firm, decided to work from his home and login remotely. Later, he anticipated that the remote connection could be exposed to session hijacking. To curb this possibility, he implemented a technique that creates a safe and encrypted tunnel over a public network to securely send and receive sensitive information and prevent hackers from decrypting the data flow between the endpoints.
What is the technique followed by Peter to send files securely through a remote connection?
Ron, a security professional, was pen testing web applications and SaaS platforms used by his company. While testing, he found a vulnerability that allows hackers to gain unauthorized access to API objects and perform actions such as view, update, and delete sensitive data of the company. What is the API vulnerability revealed in the above scenario?
Henry is a penetration tester who works for XYZ organization. While performing enumeration on a client organization, he queries the DNS server for a specific cached DNS record. Further, by using this cached record, he determines the sites recently visited by the organization's user.
What is the enumeration technique used by Henry on the organization?
Which iOS jailbreaking technique patches the kernel during the device boot so that it becomes jailbroken after each successive reboot?
A penetration tester identifies malware that monitors the activities of a user and secretly collects personal information, such as login credentials and browsing habits. What type of malware is this?
During a reconnaissance mission, an ethical hacker uses Maltego, a popular footprinting tool, to collect information about a target organization. The information includes the target's Internet infrastructure details (domains, DNS names, Netblocks, IP address information). The hacker decides to use social engineering
techniques to gain further information. Which of the following would be the least likely method of social engineering to yield beneficial information based on the data collected?
A group of hackers were roaming around a bank office building in a city, driving a luxury car. They were using hacking tools on their laptop with the intention to find a free-access wireless network.
What is this hacking process known as?
A security analyst investigates unusual east-west traffic on a corporate network. A rogue device has been physically inserted between a workstation and the switch, enabling unauthorized access while inheriting the workstation’s authenticated network state. Which evasion technique is being used?
Within the context of Computer Security, which of the following statements describes Social Engineering best?
Richard, an attacker, targets an MNC. In this process, he uses a footprinting technique to gather as much information as possible. Using this technique, he gathers domain information such as the target domain name, contact details of its owner, expiry date, and creation date. With this information, he creates a map of the organization's network and misleads domain owners with social engineering to obtain internal details of its network.
What type of footprinting technique is employed by Richard?
A penetration tester identifies malware on a system that hides its presence and gives an attacker access to administrative functions without being detected. What type of malware is this?
A large mobile telephony and data network operator has a data center that houses network elements. These are essentially large computers running on Linux. The perimeter of the data center is secured with firewalls and IPS systems.
What is the best security policy concerning this setup?
In the context of password security, a simple dictionary attack involves loading a dictionary file into a cracking application such as L0phtCrack or John the Ripper. The brute force method is slow but exhaustive. If you use both brute force and dictionary methods combined to vary words, what would you call such an attack?
In order to tailor your tests during a web-application scan, you decide to determine which web-server version is hosting the application. On using the sV flag with Nmap. you obtain the following response:
80/tcp open http-proxy Apache Server 7.1.6
what Information-gathering technique does this best describe?
One of your team members has asked you to analyze the following SOA record.
What is the TTL?
Rutgers.edu. SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch. In a MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports.
What happens when the CAM table becomes full?
Shiela is an information security analyst working at HiTech Security Solutions. She is performing service version discovery using Nmap to obtain information about the running services and their versions on a target system.
Which of the following Nmap options must she use to perform service version discovery on the target host?
Self-replicating malware causes redundant traffic, crashes, and spreads autonomously. What malware type is responsible, and how should it be handled?
Jack, a disgruntled ex-employee of Incalsol Ltd., decided to inject fileless malware into Incalsol's systems. To deliver the malware, he used the current employees' email IDs to send fraudulent emails embedded with malicious links that seem to be legitimate. When a victim employee clicks on the link, they are directed to a fraudulent website that automatically loads Flash and triggers the exploit. What is the technique used byjack to launch the fileless malware on the target systems?
Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?
You are instructed to perform a TCP NULL scan. In the context of TCP NULL scanning, which response indicates that a port on the target system is closed?
env x='(){ :;};echo exploit' bash –c 'cat /etc/passwd'
What is the Shellshock bash vulnerability attempting to do on a vulnerable Linux host?
A company’s customer data in a cloud environment has been exposed due to an unknown vulnerability. Which type of issue most likely led to the incident?
You went to great lengths to install all the necessary technologies to prevent hacking attacks, such as expensive firewalls, antivirus software, anti-spam systems, and intrusion detection/prevention tools in your company's network. You are confident that hackers will never be able to gain access. Your peer, Peter Smith, disagrees and says the presence of a “weakest link” still exposes the network.
What is Peter Smith talking about?
A Certified Ethical Hacker (CEH) is auditing a company’s web server that employs virtual hosting. The server hosts multiple domains and uses a web proxy to maintain anonymity and prevent IP blocking. The CEH discovers that the server’s document directory (containing critical HTML files) is named “certrcx” and stored in /admin/web. The server root (containing configuration, error, executable, and log files) is also identified. The CEH also notes that the server uses a virtual document tree for additional storage. Which action would most likely increase the security of the web server?
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice’s machine. From the command prompt, she types the following command:
What is Eve trying to do?
To hide the file on a Linux system, you have to start the filename with a specific character. What is the character?
what is the correct way of using MSFvenom to generate a reverse TCP shellcode for windows?
A Nessus scan reveals a critical SSH vulnerability (CVSS 9.0) allowing potential remote code execution on a Linux server. What action should be immediately prioritized?
Which of the following allows attackers to draw a map or outline the target organization's network infrastructure to know about the actual environment that they are going to hack.
During network analysis, clients are receiving incorrect gateway and DNS settings due to a rogue DHCP server. What security feature should the administrator enable to prevent this in the future?
Your company, Encryptor Corp, is developing a new application that will handle highly sensitive user information. As a cybersecurity specialist, you want to ensure this data is securely stored. The development team proposes a method where data is hashed and then encrypted before storage. However, you want an added layer of security to verify the integrity of the data upon retrieval. Which of the following cryptographic concepts should you propose to the team?
During a routine security audit, administrators found that cloud storage backups were illegally accessed and modified. What countermeasure would most directly mitigate such incidents in the future?
which of the following protocols can be used to secure an LDAP service against anonymous queries?
An organization uses SHA-256 for data integrity checks but still experiences unauthorized data modification. Which cryptographic tool can help resolve this issue?
A large corporate network is being subjected to repeated sniffing attacks. To increase security, the company’s IT department decides to implement a combination of several security measures. They permanently add theMAC address of the gateway to the ARP cache, switch to using IPv6 instead of IPv4, implement the use of encrypted sessions such as SSH instead of Telnet, and use Secure File Transfer Protocol instead of FTP.
However, they are still faced with the threat of sniffing. Considering the countermeasures, what should be their next step to enhance network security?
An ethical hacker has been tasked with assessing the security of a major corporation's network. She suspects the network uses default SNMP community strings. To exploit this, she plans to extract valuable network information using SNMP enumeration. Which tool could best help her to get the information without directly modifying any parameters within the SNMP agent’s management information base (MIB)?
In an enterprise environment, the network security team detects unusual behavior suggesting advanced sniffing techniques exploiting legacy protocols to intercept sensitive communications. Which of the following sniffing-related techniques presents the greatest challenge to detect and neutralize, potentially compromising confidential enterprise data?
Which protocol is used for setting up secure channels between two devices, typically in VPNs?
A penetration tester must enumerate user accounts and network resources in a highly secured Windows environment where SMB null sessions are blocked. Which technique should be used to gather this information discreetly?
Abel, a security professional, conducts penetration testing in his client organization to check for any security loopholes. He launched an attack on the DHCP servers by broadcasting forged DHCP requests and leased all the DHCP addresses available in the DHCP scope until the server could not issue any more IP addresses. This led to a Dos attack, and as a result, legitimate employees were unable to access the clients network. Which of the following attacks did Abel perform in the above scenario?
A penetration tester suspects that a web application's user profile page is vulnerable to SQL injection, as it uses the userID parameter in SQL queries without proper sanitization. Which technique should the tester use to confirm the vulnerability?
A computer science student needs to fill some information into a secured Adobe PDF job application that was received from a prospective employer. Instead of requesting a new document that allowed the forms to be completed, the student decides to write a script that pulls passwords from a list of commonly used passwords to try against the secured PDF until the correct password is found or the list is exhausted.
Which cryptography attack is the student attempting?
which of the following information security controls creates an appealing isolated environment for hackers to prevent them from compromising critical targets while simultaneously gathering information about the hacker?
Leverox Solutions hired Arnold, a security professional, for the threat intelligence process. Arnold collected information about specific threats against the organization. From this information, he retrieved contextual information about security events and incidents that helped him disclose potential risks and gain insight into attacker methodologies. He collected the information from sources such as humans, social media, and chat rooms as well as from events that resulted in cyberattacks. In this process, he also prepared a report that includes identified malicious activities, recommended courses of action, and warnings for emerging attacks. What is the type of threat intelligence collected by Arnold in the above scenario?
John, a professional hacker, targeted an organization that uses LDAP for accessing distributed directory services. He used an automated tool to anonymously query the IDAP service for sensitive information such as usernames. addresses, departmental details, and server names to launch further attacks on the target organization.
What is the tool employed by John to gather information from the IDAP service?
joe works as an it administrator in an organization and has recently set up a cloud computing service for the organization. To implement this service, he reached out to a telecom company for providing Internet connectivity and transport services between the organization and the cloud service provider, in the NIST cloud deployment reference architecture, under which category does the telecom company fall in the above scenario?
You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social engineering, you come to know that they are enforcing strong passwords. Passwords must be at least 8 characters and use 3 of the 4 categories (lowercase, uppercase, numbers, special characters). With your knowledge of likely user habits, what would be the fastest type of password cracking attack to run against these hash values?
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that allows session-oriented connections (Telnet) and performs the sequence prediction on the target operating system. He manages to find an active session due to the high level of traffic on the network.
What is Bob supposed to do next?
An attacker, using a rogue wireless AP, performed an MITM attack and injected an HTML code to embed a malicious applet in all HTTP connections. When users accessed any page, the applet ran and exploited many machines. Which one of the following tools the hacker probably used to inject HTML code?
Which of the following is a passive wireless packet analyzer that works on Linux-based systems?
You have gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool can change any user’s password or activate disabled Windows accounts?
An organization has automated the operation of critical infrastructure from a remote location. For this purpose, all the industrial control systems are connected to the Internet. To empower the manufacturing process, ensure the reliability of industrial networks, and reduce downtime and service disruption, the organization deckled to install an OT security tool that further protects against security incidents such as cyber espionage, zero-day attacks, and malware. Which of the following tools must the organization employ to protect its critical infrastructure?
An attacker gained escalated privileges on a critical server. What should be done FIRST to contain the threat with minimal disruption?
A technician is resolving an issue where a computer is unable to connect to the Internet using a wireless access point. The computer is able to transfer files locally to other machines, but cannot successfully reach the Internet. When the technician examines the IP address and default gateway they are both on the 192.168.1.0/24. Which of the following has occurred?
During a recent security assessment, you discover the organization has one Domain Name Server (DNS) in a Demilitarized Zone (DMZ) and a second DNS server on the internal network.
What is this type of DNS configuration commonly called?
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days, Bob denies that he had ever sent a mail. What do you want to "know" to prove yourself that it was Bob who had sent the mail?
SCADA anomalies suggest a side-channel attack. Which investigation best confirms this?
Which among the following is the best example of the third step (delivery) in the cyber kill chain?
You receive an email prompting you to download “Antivirus 2010” software using a suspicious link. The software claims to provide protection but redirects you to an unknown site.
How will you determine if this is a Real or Fake Antivirus website?
You perform a network scan using ICMP Echo Requests and observe that certain IP addresses do not return Echo Replies, while other network services remain functional. How should this situation be interpreted?
You are a cybersecurlty consultant for a smart city project. The project involves deploying a vast network of loT devices for public utilities like traffic control, water supply, and power grid management The city administration is concerned about the possibility of a Distributed Denial of Service (DDoS) attack crippling these critical services. They have asked you for advice on how to prevent such an attack. What would be your primary recommendation?
Susan, a software developer, wants her web API to update other applications with the latest information. For this purpose, she uses a user-defined HTTP tailback or push APIs that are raised based on trigger events: when invoked, this feature supplies data to other applications so that users can instantly receive real-time Information.
Which of the following techniques is employed by Susan?
Which social engineering attack involves impersonating a coworker or authority figure to extract confidential information?
As a cybersecurity consultant for SafePath Corp, you have been tasked with implementing a system for secure email communication. The key requirement is to ensure both confidentiality and non-repudiation. While considering various encryption methods, you are inclined towards using a combination of symmetric and asymmetric cryptography. However, you are unsure which cryptographic technique would best serve the purpose. Which of the following options would you choose to meet these requirements?
A penetration tester is tasked with assessing the security of a smart home IoT device that communicates with a mobile app over an unencrypted connection. The tester wants to intercept the communication and extract sensitive information. What is the most effective approach to exploit this vulnerability?
Which is the first step followed by Vulnerability Scanners for scanning a network?
A corporation migrates to a public cloud service, and the security team identifies a critical vulnerability in the cloud provider’s API. What is the most likely threat arising from this flaw?
An ethical hacker needs to gather detailed information about a company's internal network without initiating any direct interaction that could be logged or raise suspicion. Which approach should be used to obtain this information covertly?
A penetration tester targets a company's executive assistants by referencing upcoming board meetings in an email requesting access to confidential agendas. What is the most effective social engineering technique to obtain the necessary credentials without raising suspicion?
During a high-stakes engagement, a penetration tester abuses MS-EFSRPC to force a domain controller to authenticate to an attacker-controlled server. The tester captures the NTLM hash and relays it to AD CS to obtain a certificate granting domain admin privileges. Which network-level hijacking technique is illustrated?
A large enterprise has been experiencing sporadic system crashes and instability, resulting in limited access to its web services. The security team suspects it could be a result of a Denial of Service (DoS) attack. A significant increase in traffic was noticed in the network logs, with patterns suggesting packet sizes exceeding the prescribed size limit. Which among the following DoS attack techniques best describes this scenario?
You are a cybersecurity consultant for a healthcare organization that utilizes Internet of Medical Things (loMT) devices, such as connected insulin pumps and heart rate monitors, to provide improved patientcare. Recently, the organization has been targeted by ransomware attacks. While the IT infrastructure was unaffected due to robust security measures, they are worried that the loMT devices could be potential entry points for future
attacks. What would be your main recommendation to protect these devices from such threats?
The network users are complaining because their system are slowing down. Further, every time they attempt to go a website, they receive a series of pop-ups with advertisements. What types of malware have the system been infected with?
A penetration tester is tasked with identifying vulnerabilities on a web server running outdated software. The server hosts several web applications and is protected by a basic firewall. Which technique should the tester use to exploit potential server vulnerabilities?
During security awareness training, which scenario best describes a tailgating social engineering attack?
Richard, an attacker, aimed to hack loT devices connected to a target network. In this process. Richard recorded the frequency required to share information between connected devices. After obtaining the frequency, he captured the original data when commands were initiated by the connected devices. Once the original data were collected, he used free tools such as URH to segregate the command sequence. Subsequently, he started injecting the segregated command sequence on the same frequency into the loT network, which repeats the captured signals of the devices. What Is the type of attack performed by Richard In the above scenario?
When you are testing a web application, it is very useful to employ a proxy tool to save every request and response. You can manually test every request and analyze the response to find vulnerabilities. You can test parameters and headers manually to get more precise results than if using web vulnerability scanners.
What proxy tool will help you find web vulnerabilities?
Malware uses Background Intelligent Transfer Service (BITS) to evade detection. Why is BITS attractive to attackers?
Which approach should an ethical hacker avoid to maintain passive reconnaissance?
Sam is working as a system administrator In an organization. He captured the principal characteristics of a vulnerability and produced a numerical score to reflect Its severity using CVSS v3.0 to property assess and prioritize the organization's vulnerability management processes. The base score that Sam obtained after performing cvss rating was 4.0. What is the CVSS severity level of the vulnerability discovered by Sam in the above scenario?
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
An ethical hacker is hired to conduct a comprehensive network scan of a large organization that strongly suspects potential intrusions into their internal systems. The hacker decides to employ a combination of scanning tools to obtain a detailed understanding of the network. Which sequence of actions would provide the most comprehensive information about the network's status?
You are using a public Wi-Fi network inside a coffee shop. Before surfing the web, you use your VPN to prevent intruders from sniffing your traffic. If you did not have a VPN, how would you identify whether someone is performing an ARP spoofing attack on your laptop?
Identify the UDP port that Network Time Protocol (NTP) uses as its primary means of communication?
Study the Snort rule given below:
[Image shows two Snort rules with alert messages for NETBIOS DCERPC ISystemActivator bind attempt, targeting TCP ports 135 and 445. References include CVE: CAN-2003-0352.]
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet-filtering of the firewall?
During an ethical hacking exercise, a security analyst is testing a web application that manages confidential information and suspects it may be vulnerable to SQL injection. Which payload would most likely reveal whether the application is vulnerable to time-based blind SQL injection?
Which file is a rich target to discover the structure of a website during web-server footprinting?
Alex, a cloud security engineer working in Eyecloud Inc. is tasked with isolating applications from the underlying infrastructure and stimulating communication via well-defined channels. For this purpose, he used an open-source technology that helped him in developing, packaging, and running applications; further, the technology provides PaaS through OS-level visualization, delivers containerized software packages, and promotes fast software delivery. What is the cloud technology employed by Alex in the above scenario?
You are a cybersecurity analyst at a global banking corporation and suspect a backdoor attack due to abnormal outbound traffic during non-working hours, unexplained reboots, and modified system files. Which combination of measures would be most effective to accurately identify and neutralize the backdoor while ensuring system integrity?
A penetration tester was assigned to scan a large network range to find live hosts. The network is known for using strict TCP filtering rules on its firewall, which may obstruct common host discovery techniques. The tester needs a method that can bypass these firewall restrictions and accurately identify live systems. What host discovery technique should the tester use?
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm’s public-facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
HTTP/1.1 200 OK
Server: Microsoft-IIS/6
...
Which of the following is an example of what the engineer performed?
Your company performs penetration tests and security assessments for small and medium-sized businesses in the local area. During a routine security assessment, you discover information that suggests your client is involved with human trafficking.
What should you do?
Which of the following is a low-tech way of gaining unauthorized access to systems?
Steve, an attacker, created a fake profile on a social media website and sent a request to Stella. Stella was enthralled by Steve's profile picture and the description given for his profile, and she initiated a conversation with him soon after accepting the request. After a few days. Sieve started asking about her company details and eventually gathered all the essential information regarding her company. What is the social engineering technique Steve employed in the above scenario?
One customer’s malicious activity impacts other tenants. Which control would best prevent this?
While scanning with Nmap, Patin found several hosts which have the IP ID of incremental sequences. He then decided to conduct: nmap -Pn -p- -si kiosk.adobe.com www.riaa.com. kiosk.adobe.com is the host with incremental IP ID sequence. What is the purpose of using "-si" with Nmap?
During an attempt to perform an SQL injection attack, a certified ethical hacker is focusing on the
identification of database engine type by generating an ODBC error. The ethical hacker, after injecting various payloads, finds that the web application returns a standard, generic error message that does not reveal any detailed database information. Which of the following techniques would the hacker consider next to obtain useful information about the underlying database?
While analyzing logs, you observe a large number of TCP SYN packets sent to various ports with no corresponding ACKs. What scanning technique was likely used?
As an IT Security Analyst, you’ve been asked to review the security measures of an e-commerce website that relies on a SQL database for storing sensitive customer data. Recently, an anonymous tip has alerted you to a possible threat: a seasoned hacker who specializes in SQL Injection attacks may be targeting your system. The site already employs input validation measures to prevent basic injection attacks, and it blocks any user inputs containing suspicious patterns. However, this hacker is known to use advanced SQL Injection techniques. Given this situation, which of the following strategies would the hacker most likely adopt to bypass your security measures?
Fred is the network administrator for his company. Fred is testing an internal switch. From an external IP address, Fred wants to try and trick this switch into thinking it already has established a session with his computer. How can Fred accomplish this?
A penetration tester is hired to legally assess the security of a company's network by identifying vulnerabilities and attempting to exploit them. What type of hacker is this?
Sarah, a system administrator, was alerted of potential malicious activity on the network of her company. She
discovered a malicious program spread through the instant messenger application used by her team. The
attacker had obtained access to one of her teammate's messenger accounts and started sending files across
the contact list. Which best describes the attack scenario and what measure could have prevented it?
Which of the following Bluetooth hacking techniques does an attacker use to send messages to users without the recipient’s consent, similar to email spamming?
During an investigation, an ethical hacker discovers that a web application’s API has been compromised, leading to unauthorized access and data manipulation. The attacker is using webhooks and a webshell. To prevent further exploitation, which of the following actions should be taken?
A penetration tester runs a vulnerability scan and identifies an outdated version of a web application running on the company’s server. The scan flags this as a medium-risk vulnerability. What is the best next step for the tester?
During a black-box security assessment of a large enterprise network, the penetration tester scans the internal environment and identifies that TCP port 389 is open on a domain controller. Upon further investigation, the tester runs the ldapsearch utility without providing any authentication credentials and successfully retrieves a list of usernames, email addresses, and departmental affiliations from the LDAP directory. The tester notes that this sensitive information was disclosed without triggering any access control mechanisms or requiring login credentials. Based on this behavior, what type of LDAP access mechanism is most likely being exploited?
Your company was hired by a small healthcare provider to perform a technical assessment on the network.
What is the best approach for discovering vulnerabilities on a Windows-based computer?
A friend of yours tells you that he downloaded and executed a file that was sent to him by a coworker. Since the file did nothing when executed, he asks you for help because he suspects that he may have installed a Trojan on his computer.
What tests would you perform to determine whether his computer is infected?
is a set of extensions to DNS that provide the origin authentication of DNS data to DNS clients (resolvers) so as to reduce the threat of DNS poisoning, spoofing, and similar types of attacks.
A network administrator discovers several unknown files in the root directory of his Linux FTP server. One of the files is a tarball, two are shell script files, and the third is a binary file is named "nc." The FTP server's access logs show that the anonymous user account logged in to the server, uploaded the files, and extracted the contents of the tarball and ran the script using a function provided by the FTP server's software. The “ps” command shows that the “nc” file is running as process, and the netstat command shows the “nc” process is listening on a network port.
What kind of vulnerability must be present to make this remote attack possible?
Judy created a forum, one day. she discovers that a user is posting strange images without writing comments.
She immediately calls a security expert, who discovers that the following code is hidden behind those images:
What issue occurred for the users who clicked on the image?
During the enumeration phase. Lawrence performs banner grabbing to obtain information such as OS details and versions of services running. The service that he enumerated runs directly on TCP port 445.
Which of the following services is enumerated by Lawrence in this scenario?
Sam is a penetration tester hired by Inception Tech, a security organization. He was asked to perform port scanning on a target host in the network. While performing the given task, Sam sends FIN/ACK probes and determines that an RST packet is sent in response by the target host, indicating that the port is closed.
What is the port scanning technique used by Sam to discover open ports?
As an IT security analyst, you perform network scanning using ICMP Echo Requests. During the scan, several IP addresses do not return Echo Replies, yet other network services remain operational. How should this situation be interpreted?
During a security assessment, an attacker identifies a flaw in a multi-user file system. The system first verifies access rights to a temporary file created by a user. However, immediately after this verification, and before the file is processed, the attacker manages to swap the original file with a malicious version. This manipulation happens in the brief interval between the system's access verification and the moment it handles the file, resulting in the malicious file being treated as legitimate. Which vulnerability is the attacker exploiting?
A "Server-Side Includes" attack refers to the exploitation of a web application by injecting scripts in HTML pages or executing arbitrary code remotely.
Which web-page file type, if it exists on the web server, is a strong indication that the server is vulnerable to this kind of attack?
You are a cybersecurity specialist at CloudTech Inc., a company providing cloud-based services. You are managing a project for a client who wants to migrate their sensitive data to a public cloud service. To comply with regulatory requirements, the client insists on maintaining full control over the encryption keys even when the data is at rest on the cloud. Which of the following practices should you implement to meet this requirement?
Louis, a professional hacker, had used specialized tools or search engines to encrypt all his browsing activity and navigate anonymously to obtain sensitive/hidden information about official government or federal databases. After gathering the information, he successfully performed an attack on the target government organization without being traced. Which of the following techniques is described in the above scenario?
A company hires a hacker to test its network security by simulating real-world attacks. The hacker has permission and operates within legal boundaries. What is this type of hacker called?
A cybersecurity research team identifies suspicious behavior on a user’s Android device. Upon investigation, they discover that a seemingly harmless app, downloaded from a third-party app store, has silently overwritten several legitimate applications such as WhatsApp and SHAREit. These fake replicas maintain the original icon and user interface but serve intrusive advertisements and covertly harvest credentials and personal data in the background. The attackers achieved this by embedding malicious code in utility apps like video editors and photo filters, which users were tricked into installing. The replacement occurred without user consent, and the malicious code communicates with a command-and-control (C&C) server to execute further instructions. What type of attack is being carried out in this scenario?
An ethical hacker is conducting a penetration test on a company’s network with full knowledge and permission from the organization. What is this type of hacking called?
A company’s policy requires employees to perform file transfers using protocols which encrypt traffic. You suspect some employees are still performing file transfers using unencrypted protocols because the employees do not like changes. You have positioned a network sniffer to capture traffic from the laptops used by employees in the data ingest department. Using Wireshark to examine the captured traffic, which command can be used as display filter to find unencrypted file transfers?
Which of the following statements about a zone transfer is correct? (Choose three.)
Becky has been hired by a client from Dubai to perform a penetration test against one of their remote offices. Working from her location in Columbus, Ohio, Becky runs her usual reconnaissance scans to obtain basic information about their network. When analyzing the results of her Whois search, Becky notices that the IP was allocated to a location in Le Havre, France. Which regional Internet registry should Becky go to for detailed information?
CEH v13 |


