Refer to the exhibit.

A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2 The number of client entries per returned page is restricted to 1.000 according to the API specification Network 2 has 2.500 clients What must be added where the code is missing to print the content of each response?
A)

B)

C)

D)

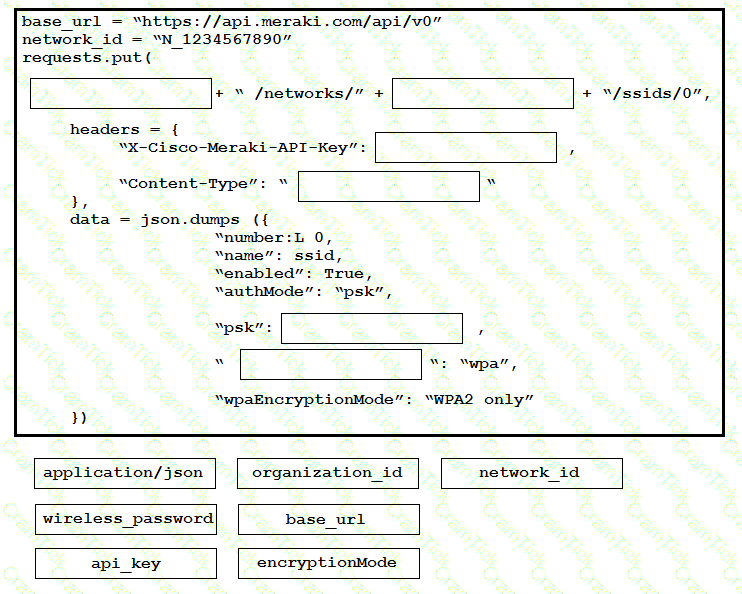
Drag and drop the code onto the snippet to update a SSID in Meraki using the Dashboard API. Not all options are used.
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image in each of the relevant clouds and can be given an identity and all required configuration via cloud-init without needing to log into the VM once online.
Which configuration management and/or automation tooling is needed for this solution?
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
A developer releases a new application for network automation of Cisco devices deployed m a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability-driven development lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
The response from a server includes the header ETag: W/”7eb8b94419e371767916ef13e0d6e63d”. Which statement is true?
Refer to the exhibit.

A developer created a Python script to retrieve interface information for the devices in a MeraKi network environment. A security analyst has reviewed the code and observed poor secret storage practices. What is the appropriate password storage approach?
A developer in a learn of distributed authors is working on code in an isolated Git branch named 'update4a2f5464771 The developer attempts to merge the new code with a branch named ’dvcapp2a3f1564733' however the merge operation encounters a conflict error during the process. Which Git command must the developer use to exit from the merge process and return the branch to the previous state?
Refer to the exhibit.
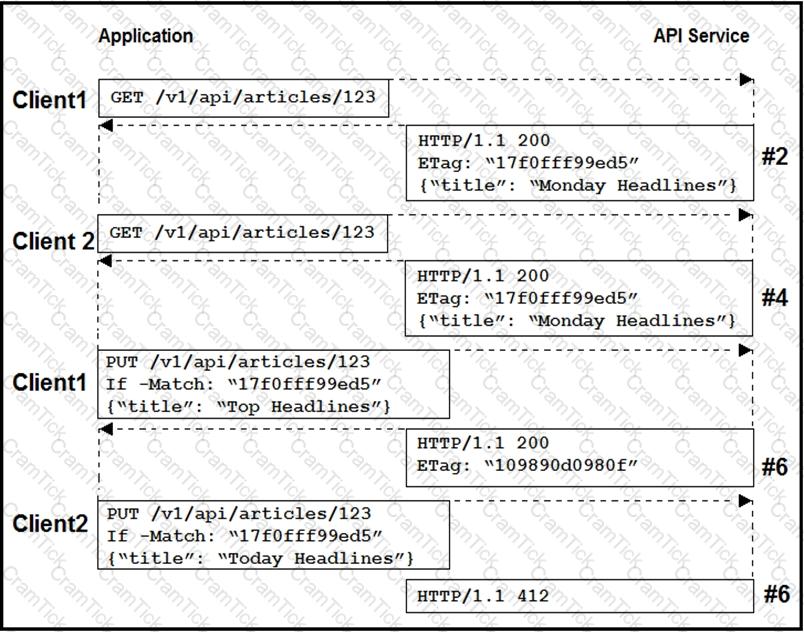
Two editors are concurrently updating an article’s headline from their mobile devices. What results from this scenario based on this REST API sequence?
Refer to the exhibit.
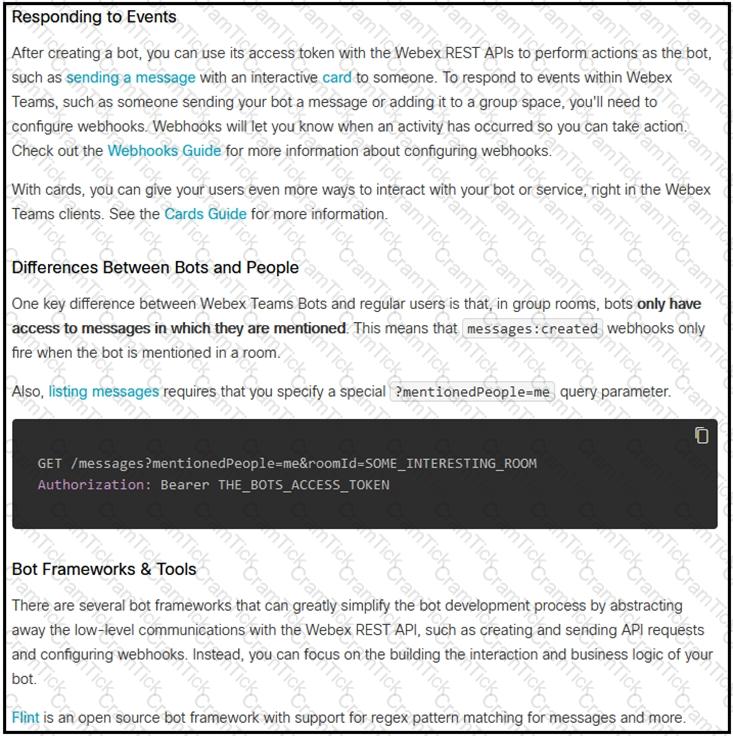
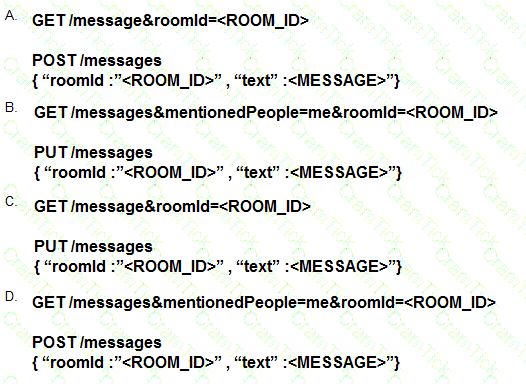
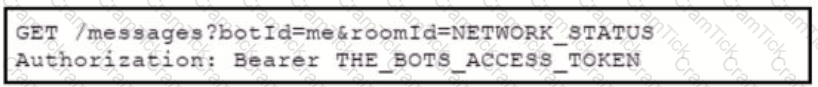
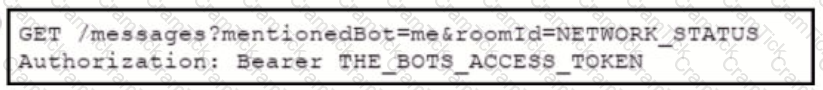
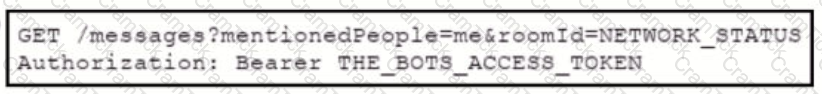
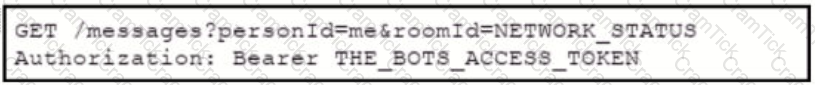
Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
An application is developed in order to communicate with Cisco Webex. For reporting, the application must retrieve all the messages sent to a Cisco Webex room on a monthly basis.
Which action calls /v1/messages directly?
Refer to the exhibit. Which snippet creates a Webex Teams space and adds the users in the variable user list to that space?
A)
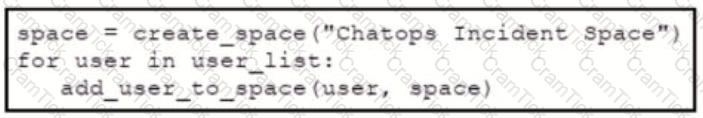
B)
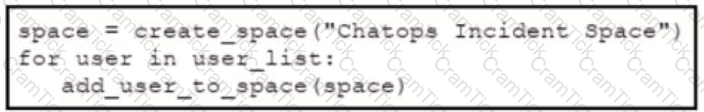
C)
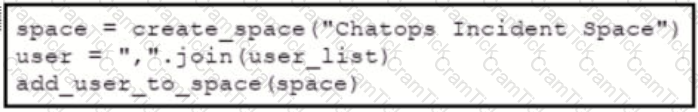
D)
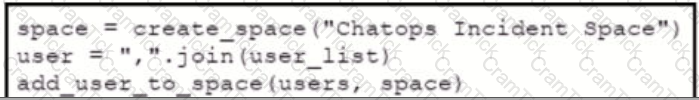
A new record-keeping application for employees to track customer orders must be deployed to a company's existing infrastructure. The host servers reside in a data center in a different country to where the majority of users work. The new network configuration for the database server is: •IP: 10.8.32.10
• Subnet Mask: 255.255.255.0
• Hostname: CustOrd423320458-Prod-010
• MAC: 18-46-AC-6F-F4-52.
The performance of the client-side application is a priority due to the high demand placed on it by employees. Which area should the team consider in terms of impact to application performance due to the planned deployment?
A developer deploys a web application in a local data center that is now experiencing high traffic load from users accessing data through REST API calls. Which approach enhances the responsiveness and performance of the API?
Refer to the exhibit
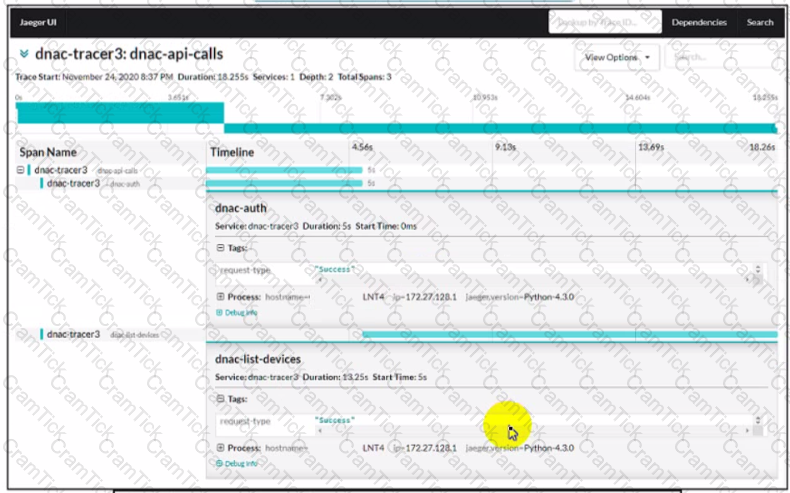

An application is developed to perform multiple API calls. The calls will be performed on the infrastructure devices Delays in the information transfer occur when the application is executed What are two reasons for the issue? (Choose two )
Refer to the exhibit.
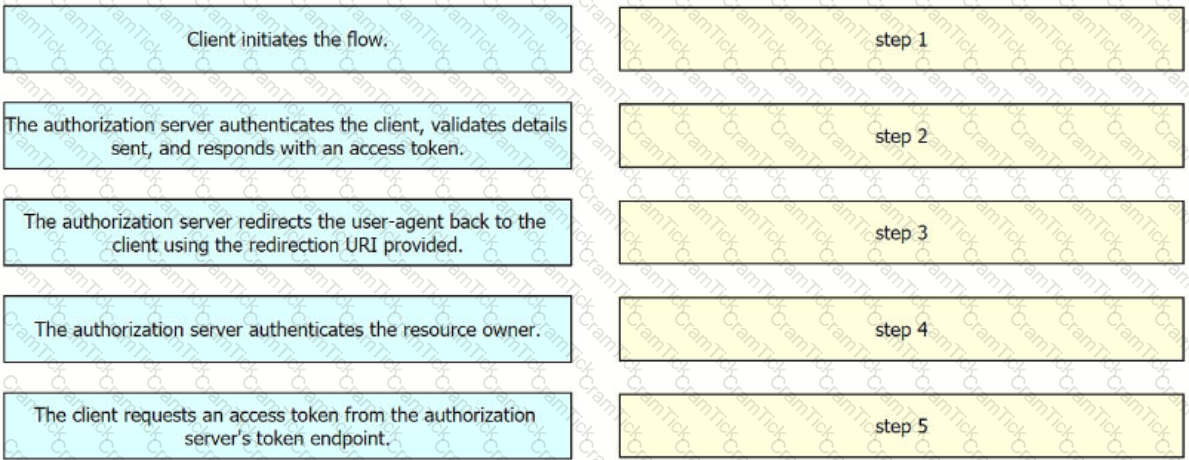
Drag and drop the steps from the left into the order of operation on the right for a successful OAuth2 three-legged authorization code grant flow,
A developer is deploying an application to automate the configuration and management of Osco network files and routers The application must use REST API interface lo achieve programmability. The security team mandates that the network must be protected against DDoS attacks What mitigates the attacks without impacting genuine requests?
A container running a Python script is failing when it reaches the integration testing phase of the CI/CD process. The code has been reviewed thoroughly and the build process works on this container and all other containers pass unit and integration testing.
What should be verified to resolve the issue?
A developer must deploy a containerized application foe network device inventory management. The developer sets up a Kubernetes duster on two separate hypervisors. The SLA is not currently meeting a specified maximum value for network latencyjitter CPU/memory and disk I/O are functioning property. Which two design approaches resolve the issue'' (Choose two.)
A cloud native project is being worked on in which all source code and dependencies are written in Python, Ruby, and/or JavaScipt. A change in code triggers a notification to the CI/CD tool to run the CI/CD pipeline.
Which step should be omitted from the pipeline?
Which two gRPC modes of model-driven telemetry are supported on Cisco IOS XE Software? (Choose two.)
A developer IS deploying an action to automate the configuration and management of Cisco network switches and routers. The application must use REST API interlace to achieve programmability. The security team mandates that the network must be protected against DDoS attacks. What mitigates the attacks without impacting genuine requests?
A developer needs to configure an environment to orchestrate and configure. Which two tools should be used for each task? (Choose two.)
Refer to the exhibit.
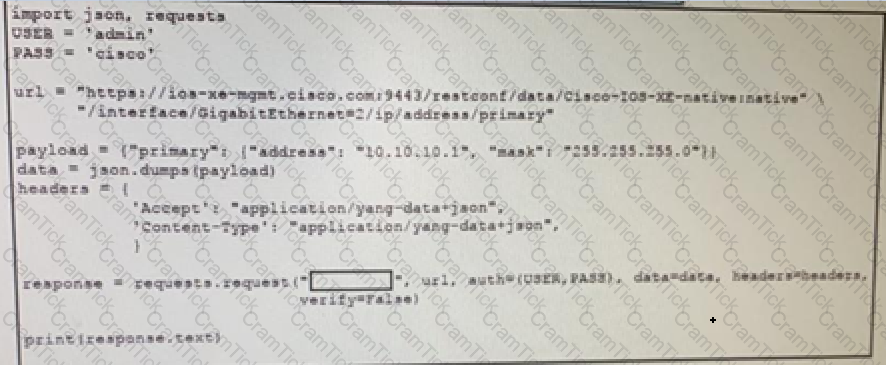
Which RESTCONF verb changes the GigabitEthernet2 interface from 192.168.100.1/24 to 10.10.10.1/24
Which OAuth mechanism enables clients to continue to have an active access token without further interaction from the user?
A bot has been created, called "386231131”, to respond to alarm messages. A developer is now creating a Webhook to allow the bot to respond to messages. Which format allows the Webhook to respond to messages for the bot within Webex Teams?
A)
B)
C)
D)


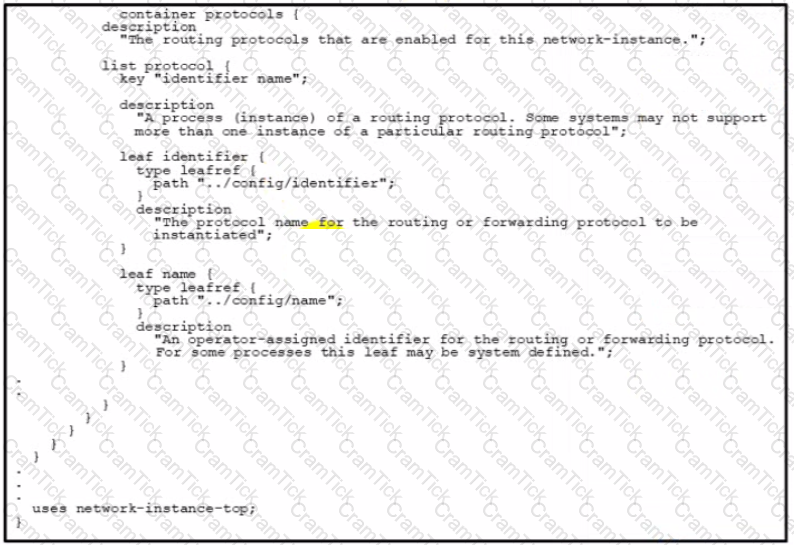
Refer to the exhibit above and click on the IETF Routing tab in the top left corner to help with this question. A developer is trying to update the routing instance by adding a new route to the routes list using the URL in the exhibit. What action must be taken to fix the error being received?
Refer to the exhibit.
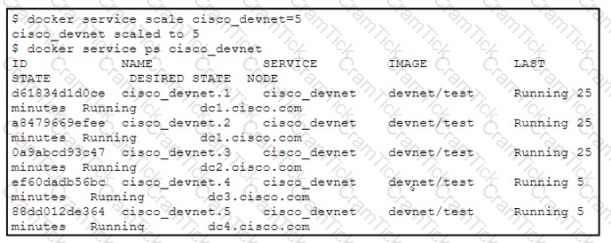
A developer runs the docker service scale command to increase the number of replicas for the cisco_devnet service. The swarm cluster is using a private IP address subnet. The service has these design requirements:
Which design approach is used to fulfill the requirements?
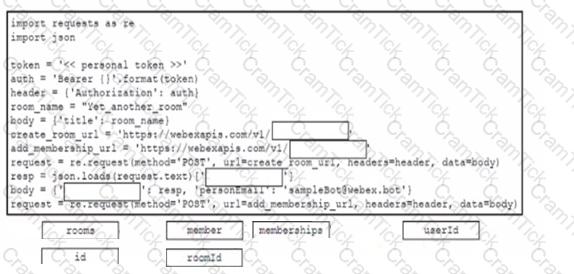
Drag and drop the code from the bottom onto the box where the code is missing to create a new Cisco Webex space and attach a previously configured bot named 'sampleBot'. Not all options are used.
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
Refer to the exhibit.
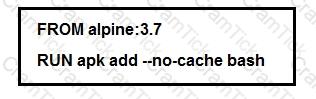
Which additional line results in the output of Test 1 upon execution of the docker run --rm devnet 1 command in a Dockerfile with this content?
Drag and drop the code snippets from the bottom onto the boxes where the code is missing to deploy three Cisco UCS servers each from a different template Not all options ate used.
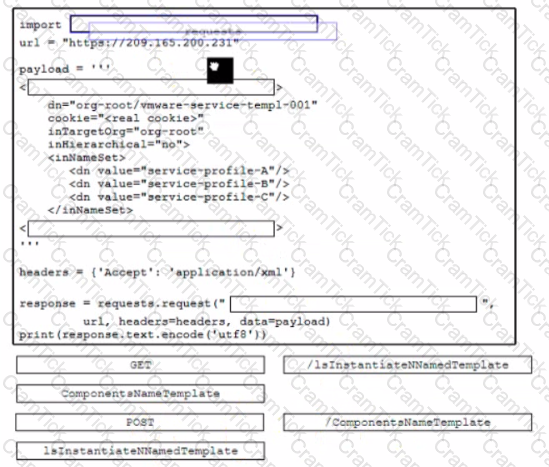
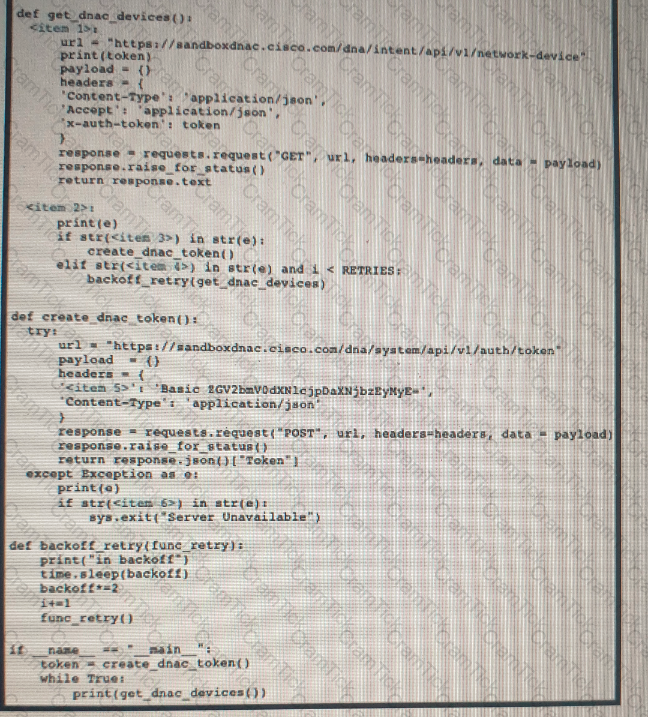
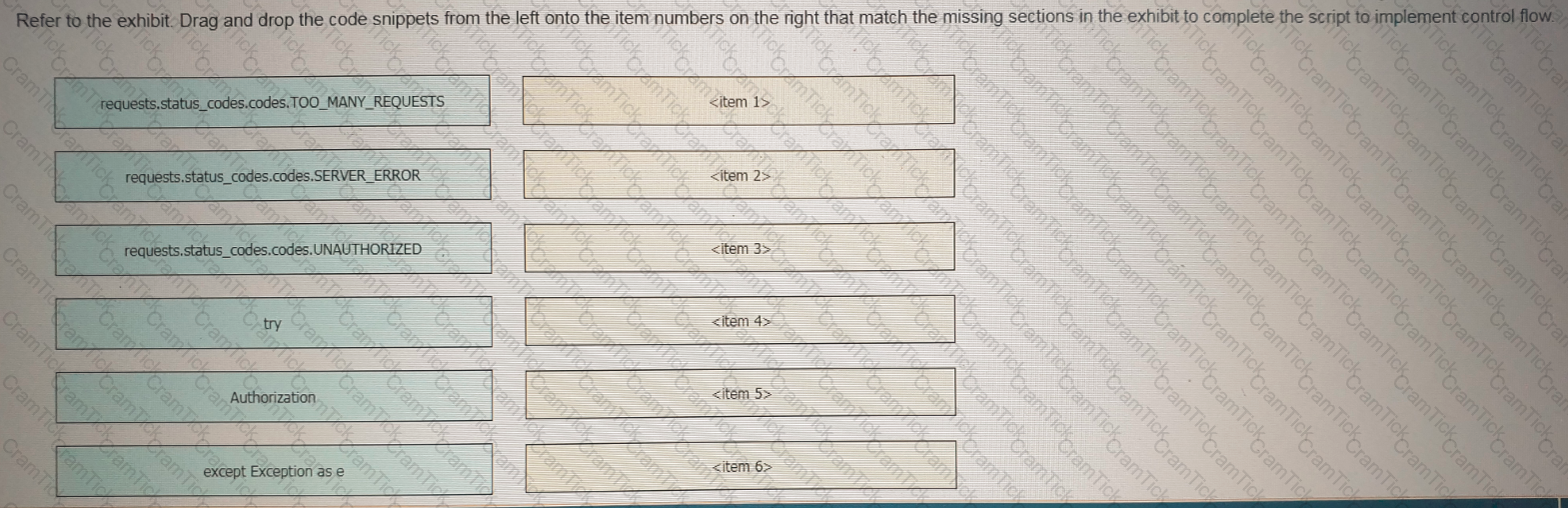
Refer to the exhibit Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
Refer to the exhibit.

An application is created to serve an enterprise Based on use and department requirements, changes are requested quarterly Which application design change improves code maintainability?
Refer to the exhibit.
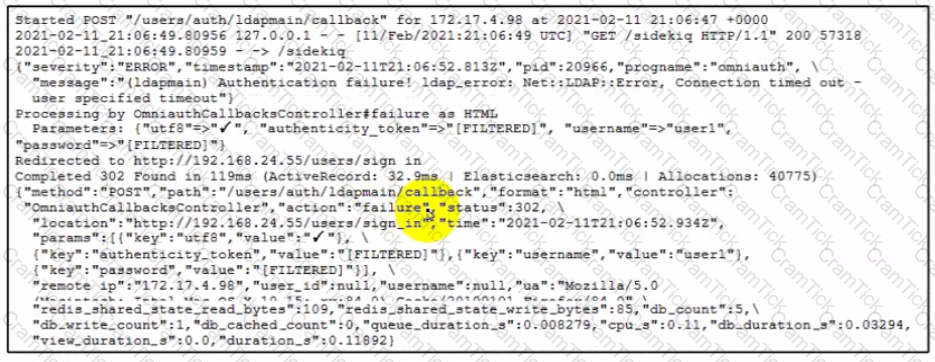
Recently, users have reported problems logging into an application with their usernames and passwords. The logs have captured an authentication attempt. Based on the messages and errors contained, what is the cause of the problem?
An engineer needs to configure an interface named GigabitEthernet3 with an IP address on several RESTCONF-enabled Cisco IOS XE devices. Which code snippet must be placed in the blank in the code to meet this requirement?
A developer plans to create a new bugfix branch to fix a bug that was found on the release branch. Which command completes the task?
In the three-legged OAuth2 process, after the authorization server presents a form to the resource owner to grant access, what is the next step?
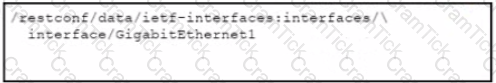
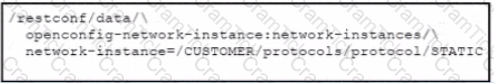
Refer to the exhibit. Which URI string retrieves configured static routes in a VRF named CUSTOMER from a RESTCONF-enabled device?
A)

B)
C)

D)
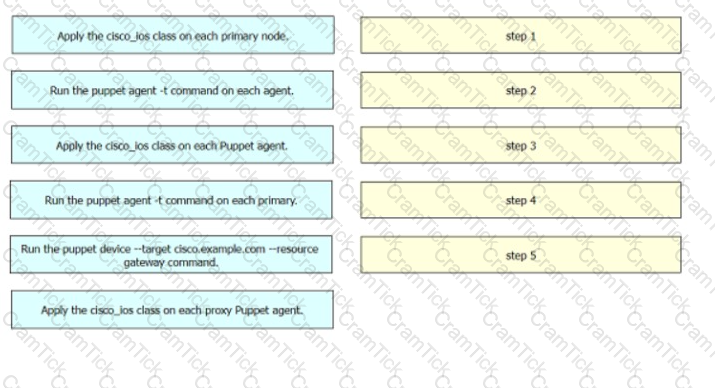
Drag and drop the steps from the left into the order on the right to create the workflow to retrieve the gateway information from a set of Cisco IOS devices. Not all options are used.
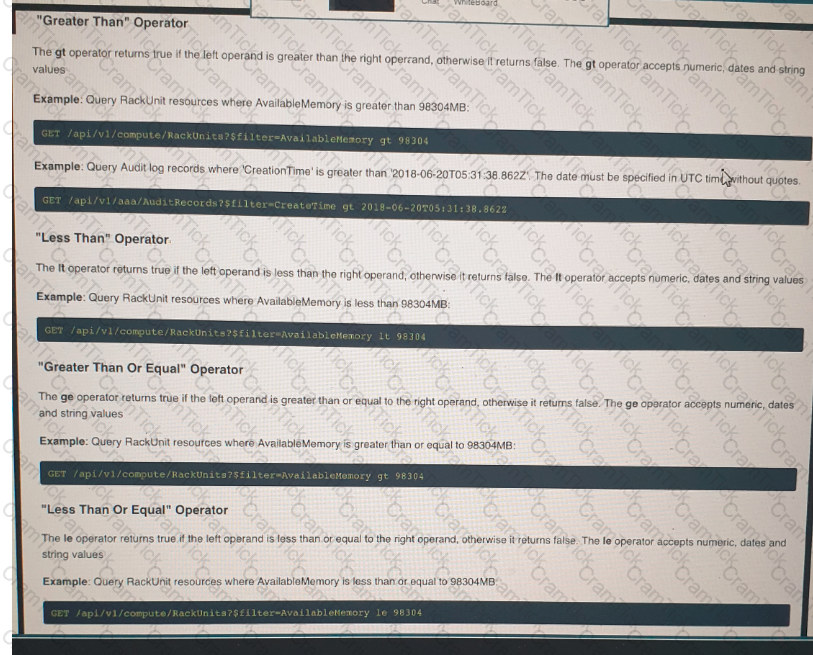
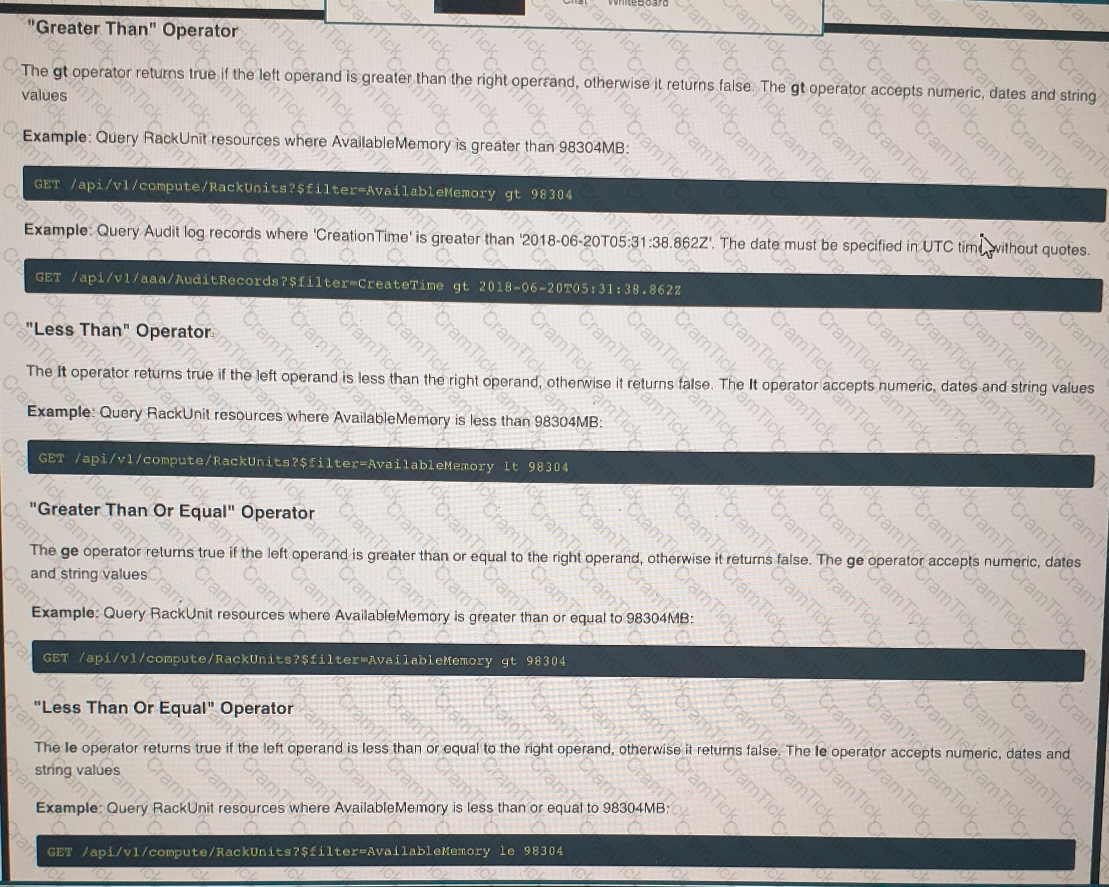
Click on the GET Resource button above to view resources that will help with this question. An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB. Which REST API call accomplishes this task?
A team is developing a cloud-native application for network monitoring and management of various devices. An increased growth rate of users is expected. The solution must be easily managed and meet these requirements:
•able to use dependencies
•easy disposability
•flexible configuration
Which application design approach must be used?
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
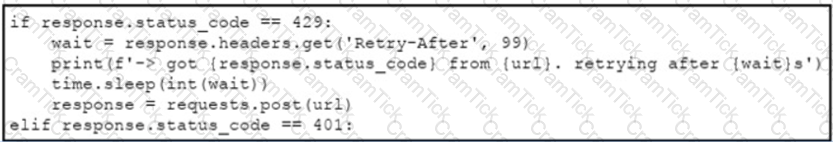
Refer to the exhibit.
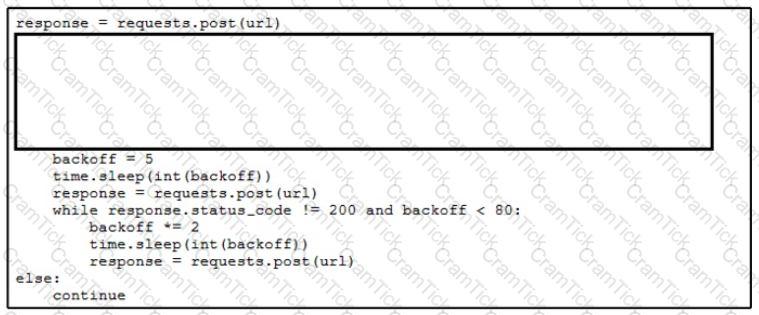
An engineer needs to implement REST API error handling when a timeout or rate limit scenario is present. Which code snippet must be placed into the blank in the code to complete the API request?
A)
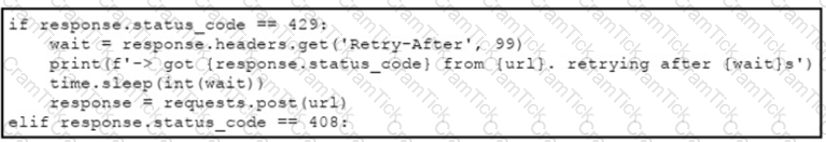
B)
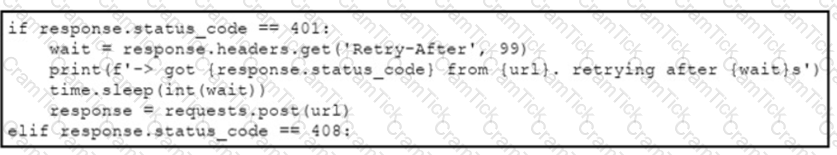
C)
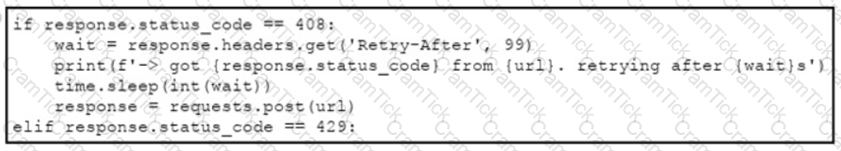
D)
Cisco Certified DevNet Professional | 350-901 Written Exam | 350-901 Questions Answers | 350-901 Test Prep | 350-901 Cisco Certified DevNet Professional Actual Questions | Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Exam Questions PDF | 350-901 Online Exam | 350-901 Practice Test | 350-901 PDF | 350-901 Cisco Certified DevNet Professional Dumps | 350-901 Test Questions | 350-901 Study Material | 350-901 Exam Preparation | 350-901 Valid Dumps | 350-901 Real Questions | 350-901 Cisco Certified DevNet Professional Practice Test | Cisco Certified DevNet Professional 350-901 Dumps | Developing Applications using Cisco Core Platforms and APIs (DEVCOR) Exam Questions


