A Linux administrator needs to configure a user account to notify the user ten days before the password will expire. Which of the following commands would BEST accomplish this task?
A company wants to ensure that all newly created files can be modified only by their owners and that all new directory content can be changed only by the creator of the directory. Which of the following commands will help achieve this task?
Which of the following can be used to boot a DVD from a remote device to initialize a Linux system setup on bare metal hardware as if it is a local DVD?
A junior Linux administrator is installing patches using YUM. The administrator issues the following command:
yum list installed
The output of the command is as follows:
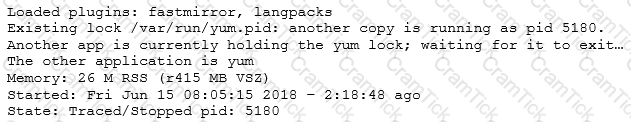
Given this scenario and the output, which of the following should the administrator do to address this issue?
A Linux administrator is getting an error message indicating a device does not have any space left on it. However, the administrator runs the following commands and receives the output below:
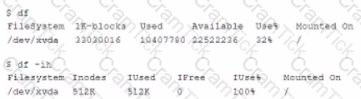
Which of the following is the MOST likely cause of the issue?
Which of the following is commonly implemented in external devices to provide unique event-based two-factor authentication credentials when a system is already implementing username and password authentication?
Ann, a Linux administrator, wants to edit a configuration management file. When she opens the file to edit, her text editor reports that the file has been opened in read-only mode. She then tries to edit the file as root by elevating via sudo and is still unable to save any changes. The error message in her text editor says that the read-only option is set on the file. Ann checks the permissions on the file and sees the following:
-rw-rw-r-- 1 root wheel 30 Jun 13 15:38 infrastructure.yml
Which of the following commands is the BEST option to allow her to successfully modify the file?
A Linux system is running normally when the systems administrator receives an alert that one application spawned many processes. The application is consuming a lot of memory, and it will soon cause the machine to become unresponsive. Which of the following commands will stop each application process?
An administrator receives a warning about a file system filling up, and then identifies a large file located at /tmp/largelogfile. The administrator deletes the file, but no space is recovered on the file system.
Which of the following commands would BEST assists the administrator in identifying the problem?
A user does not want Bluetooth to start up every tme the system starts. Which of the following commands should the user execute to accomplish this task?
A systems administrator needs to retrieve specific fields from a csv file. Which of the following tools would accomplish this task?
A systems administrator is unable to reach other devices on the network and the Internet. The server is configured with the IP address 192.169.1.50/24 on eth0. The server’s router is 192.168.1.1. The administrator reviews the output of route –n:
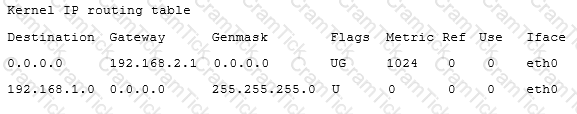
Which of the following commands should the administrator run to correct the issue?
A Linux administration is using a Linux system as a router. During the tests, the administrator discovers that IP packets are not being sent between the configured interfaces.
Which of the following commands enables this feature for IPv4 networks?
A systems administrator is attempting to access a server by SSH. The Linux administrator ensures that the SSH keys on the remote server were unable to connect. The following error message is being displayed:
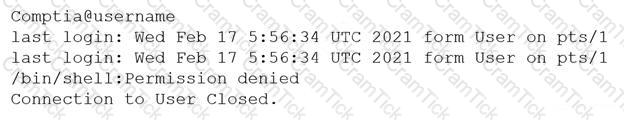
Which of the following needs to be changed on order for the administrator to access the server via SSH?
A security team informs the Linux administrator that a specific sever is acting as a n pen relay. To which of the following is the security team referring?
An administrator needs to set the time of a VM that has no network connectivity to an NTP server. The VM’s host, however, is synchronized with NTP.
Which of the following allows the administrator to synchronize the time of the VM with the host?
Which of the following configuration files should be modified to disable Ctrl-Alt-Del in Linux?
An administrator notices that a long-running script, /home/user/script.sh, is taking up a large number of system resources. The administrator does not know the script’s function. Which of the following commands should the administrator use to minimize the script’s impact on system resources?
A Linux server hosts Kerberos and LDAP, which of the following is the MOST likely role of this server?
Which of the following server roles is MOST appropriate to route files to multifunction devices?
A systems administrator is investigating low performance a server. After executing some diagnostic commands, the administrator analyzes the data:
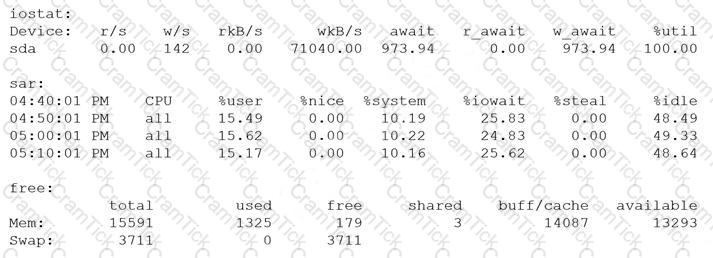
Which of the following is the cause of low performance on the server?
An administrator is utilizing an automation engine that engine that uses SSH to run command on remote systems. Which of the following does this describe?
A Linux administrator has configured a local named caching server to reduce the amount of time to resolve common DNS addresses. The server resolves using the external server, however; the administrator wants to avoid this configuration. The administrator verifies the named, conf settings to confirm the following relevant settings:
The administrator then runs dig twice to look up an external address and receives the following relevant output the second time.
Which of the following should the administrator do to correct the configuration?
A Linux systems administrator needs to set permissions on an application with the following parameters:
The owner of the application should be able to read, write, and execute the application.
Members of the group should be able to read and execute the application.
Everyone else should not have access to the application.
Which of the following commands would BEST accomplish these tasks?
Joe is no longer employed by a company and Ann is tatang over his protects several team members work out of the project directory inducing Ann. The administrator needs to assign ownership of all of Joe's files in the /project directory to Ann. Which of the following should the administrator run to accomplish this task?
A four-drive Linux NAS has been improperly configured. Each drive has a capacity of 6TB, for a total storage capacity of 24TB. To reconfigure this unit to be not pluggable for drive replacement and provide total storage of 11TB to 12TB, which of the following would be the correct RAID configuration?
An administrator is logged on as an unprivileged user and needs to compile and installed an application from source. Which of the following BEST represents how to complete this task?
A new packages repository named repo10 has been installed on mirror site. A Linux administrator wants to use this new repository for local package installations. In which of the following locations should the administrator store the configuration information for the repo10 repository?
When logging in, an administrator must use a temporary six-digit code that is displayed on a key fob.
Which of the following has been implemented?
A systems administrator a retting an HTTPO server on a Lnux server and configuring as a proxy server The administrator runs the following commands to venfy that the service is running:

However, the arjminrstraior is getting a 503 error when browsing to portal.company. internal. After reviewing the logs, the following error information is discovered:

Which of the following commands BEST resolves the issue?
Joe, a user, creates a short shell script, shortscript.sh, and saves it in his home directory with default
permissions and paths. He then attempts to run the script by typing ./shortscript.sh, but the command
fails to execute.
Which of the following commands would have allowed the script to run?
A junior systems administrator needs to make a packet capture file that will only capture HTTP protocol data to a file called test.pcap.
Which of the following commands would allow the administrator to accomplish this task?
A user wants to alias dir so it always returns the contents of the ls -la command. However, the user has to
reset the alias with every login.
Which of the following is the BEST action the user can take to ensure the command is always available?
A user requested a USB serial device to be added to a desktop computer. The device has built-in kernel driver
support. The administrator tested the device installation and access, but the user cannot access the serial port.
Each time the user attempts to access the device, an error log is created that shows the user does not have
permission to use the serial port. Which of the following will add a user to the group that has serial port
capabilities?
On a UEFI-based system, which of the following invokes GRUB2 from the EFI command prompt?
An administrator needs to kill the oldest Bash shell running in the system. Which of the following commands
should be issued to accomplish this task?
A Linux administrator needs to disable the Sendmail service on a Linux server and prevent it from being started manually and during boot.
Which of the following is the BEST command to do this?
A security team informs the Linux administrator that a specific server is acting as an open relay.
To which of the following is the security team referring?
A Linux user wants to give read-only permissions to a directory and its contents. Which of the following
commands will allow the user to accomplish this task?
A systems administrator is receiving errors while trying to install a popular virtualization software. The software
specifications state the processor needs to support virtualization with Intel instructions. Additional requirements
state the processor must accelerate encryption/decryption and use hyperthreading. Given the following output
about the processor:
fpu ume depse tsu msr pae mce cx8 apic sep mtrr pae mca cmov pat pse36 cflusm mmx
fxsr sse sse2 ht syscall nx rdtscp lm constant_tsc rep_good nopl xtopology
nonstop_tsc pni pclmulqdq ssse3 cx16 pcid sse4_1 sse4_2 x2apic popcnt aes xsave
avx rdrand hypervisor lahf_lm fsgsbase
Which of the following is the MOST likely reason for the errors?
A new IO card has been added to the security server to log the opening and closing of the main entrance. A
switch is attached, so the interface card returns a 1 when the door is opened and a 0 when the door is closed.
Which of the following describes the Linux device to which this switch is attached?
A Linux administrator is testing a configuration script and wants to change the hostname of a workstation temporarily, but it must return to its assigned workstation name after reboot. Which of the following is the BEST command for the administrator to use?
Which of the following Linux server roles should be installed to monitor and log local web traffic?
A systems administrator wants to disable the isofs module on the server.
Which of the following will allow the administrator to check if the isofs module is currently in use?
A technician wants to secure a sensitive workstation by ensuring network traffic is kept within the local subnet. To accomplish this task, the technician executes the following command:
echo 0 > /proc/sys/net/ipv4/ip_default_ttl
Which of the following commands can the technician use to confirm the expected results? (Choose two.)
In which of the following Linux GUI environments would the Konsole application MOST likely be found?
A Linux administrator is developing a Bash script to close specific ports on a server firewall. The administrator is not certain of the default port for the Internet Message Access Protocol.
Which of the following files should the administrator check to determine the default port?
A junior administrator is migrating a virtual machine from a Type 1 hypervisor to a Type 2 hypervisor. To ensure portability, which of the following formats should the administrator export from the Type 1 hypervisor to ensure compatibility?
After cloning a remote repository, a new feature of that project needs to be developed and integrated into the next major release.
Which of the following is the first Git operation to run to begin working on this new feature immediately after the clone?
A security administrator wants to display a warning banner before a user logs in. Which of the following files must be edited to make this happen?
Which of the following commands allow an administrator to determine if the current system is a virtual machine?
An administrator needs to examine two text files and select identical lines from the files. Which of the following commands wooW BEST accomplish this task?
An administrator needs to copy files from a Samba share where the server name is accounting. local, the share is reports, and the username is admin. Assuming local directories exist, which of the following commands would connect to the share?
A systems administrator needs to prevent the root account from being used to log in to a Linux server via SSH. Which of the following configuration ies does the systems administrator need to edit to perform this task?
A systems administrator would like to back up all of the'. conf' files on a server The administrator runs the command:
Find / --name ‘’*conf’’ > backup,tar
After investigating the backup, tar file the administrator realizes that the contents of the configuration files were not backed up property. Which of the following would BEST accomplish this task?
A Linux administrator needs to schedule a backup job to run every Friday at 2 15 a.m. Which of the following lines should the administrator add to the crontab file?
A Linux administrator executed 1vextend to expand disk space to a partition from 8GB to 40GB However, the filesystem is not showing the additional space The administrator runs several commands and rectyes the following output:
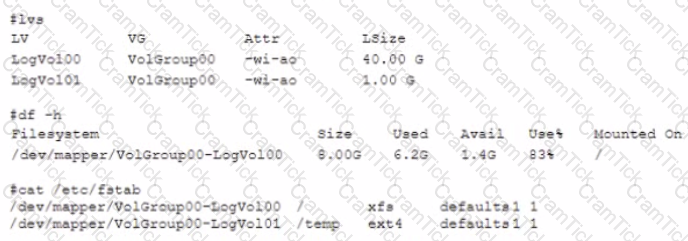
Which of the following commands should the administrator run to resolve the issue?
A developer has contacted a systems administrator because an application is not receiving a response from the client. The application must purge the message queue before terminating. Which of the following should the systems administrator perform in order to BEST address the issue?
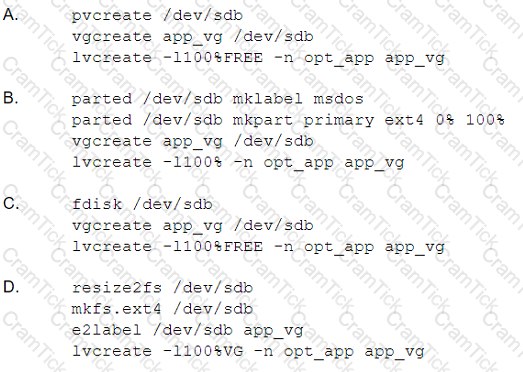
A systems administrator is creating a new volume opt _ app in a volume group app_vg. The new volume should utilize all the available disk space from the newly added disk device /dev/ sdb. Which of the following will achieve
the task, assuming the app_vg volume group does not exist yet and the disk device was added but not configured?
Whenever an administrator merges the feature branch into master, a binary is created and saved in the artifact repository. Which of the following does this desenbe?
An end user is trying to execute a file within a different directory The end user executes the following command:
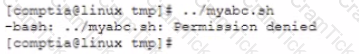
Which of the following commands should the Linux administrator use to run the shell scnpt within that folder?
A developer wrote a custom version of the /bin/password command and placed it in /usr/local/bin/password. The new command needs to write to the /etc/paaawd file even when executed by a regular user. Which of the following commands should the administrator run to set the proper file permissions on this file?
A)
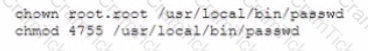
B)
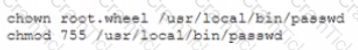
C)

D)

A user is unable to execute the command sudo su -on a newly provisioned system. Which of the following should the Linux administrator do to allow the user to execute that command?
Which of the following is a file that can define how to build, deploy, and install various components for a Linux application hosted in a cloud environment?
Which of the following techniques would BEST ensure the setup and desired state of a server are consistently maintained?
A security audit concludes that an organization's database servers need to be hardened As a result, an administrator obtans tie fofcjwwng partial Nmap output from a database server.
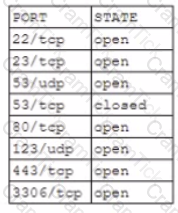
Which of the following commands should the administrator execute to mitigate security risks?
An administrator is troubleshooting an issue where end users are waiting a very long times for processes to respond. The top command reveals that multiple processes seem to be m a non-responsive state or have become zombies. Which of the administrator use to clean up the system?
Linux+ | XK0-004 Questions Answers | XK0-004 Test Prep | CompTIA Linux+ Certification Exam Questions PDF | XK0-004 Online Exam | XK0-004 Practice Test | XK0-004 PDF | XK0-004 Test Questions | XK0-004 Study Material | XK0-004 Exam Preparation | XK0-004 Valid Dumps | XK0-004 Real Questions | Linux+ XK0-004 Exam Questions