A network administrator is setting up Cisco FMC to send logs to Cisco Security Analytics and Logging (SaaS). The network administrator is anticipating a high volume of logging events from the firewalls and wants lo limit the strain on firewall resources. Which method must the administrator use to send these logs to Cisco Security Analytics and Logging?
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection?
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices The default management port conflicts with other communications on the network and must be changed What must be done to ensure that all devices can communicate together?
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
Due to a traffic storm on the network, two interfaces were error-disabled, and both interfaces sent SNMP traps.
Which two actions must be taken to ensure that interfaces are put back into service? (Choose two)
A security administrator is designing an email protection solution for an onsite email server and must meet these requirements:
Remove malware from email before it reaches corporate premises
Drop emails with risky links automatically
Block access to newly infected sites with real-time URL analysis
Which solution must be used?
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
What can be integrated with Cisco Threat Intelligence Director to provide information about security threats,
which allows the SOC to proactively automate responses to those threats?
v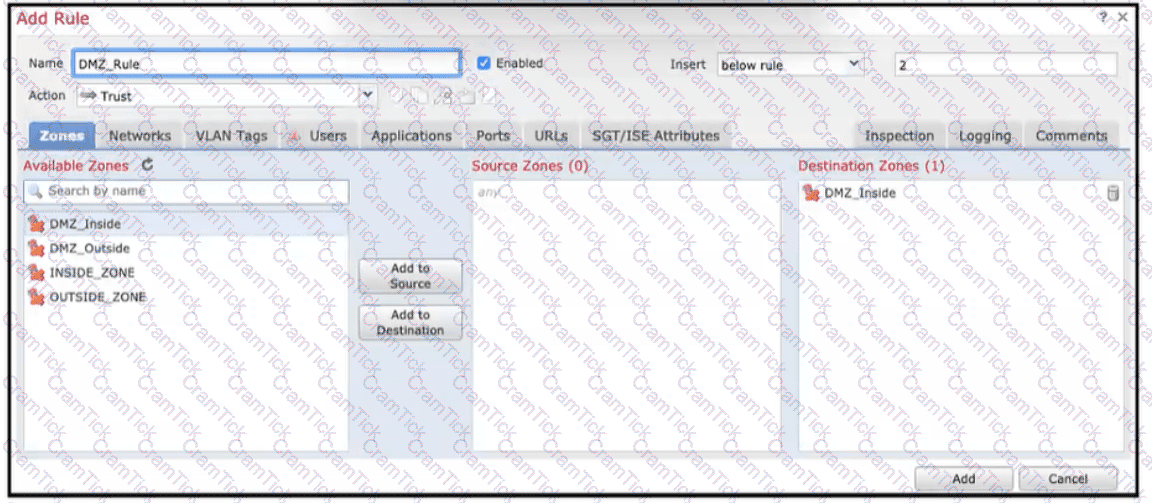
Refer to the exhibit When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZjnside zone once the configuration is deployed?
Which solution is made from a collection of secure development practices and guidelines that developers must follow to build secure applications?
An engineer wants to generate NetFlow records on traffic traversing the Cisco ASA. Which Cisco ASA
command must be used?
When wired 802.1X authentication is implemented, which two components are required? (Choose two)
Which RADIUS feature provides a mechanism to change the AAA attributes of a session after it is
authenticated?
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this
requirement using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor?
An engineer is configuring 802.1X authentication on Cisco switches in the network and is using CoA as a mechanism. Which port on the firewall must be opened to allow the CoA traffic to traverse the network?
With which components does a southbound API within a software-defined network architecture communicate?
A company discovered an attack propagating through their network via a file. A custom file policy was created in order to track this in the future and ensure no other endpoints execute the infected file. In addition, it was discovered during testing that the scans are not detecting the file as an indicator of compromise. What must be done in order to ensure that the created is functioning as it should?
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to
network resources?
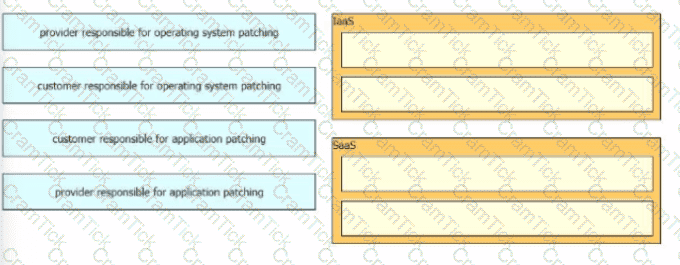
Drag and drop the security responsibilities from the left onto the corresponding cloud service models on the right.
Which threat involves software being used to gain unauthorized access to a computer system?
What is a benefit of using Cisco AVC (Application Visibility and Control) for application control?
An engineer needs to configure an access control policy rule to always send traffic for inspection without
using the default action. Which action should be configured for this rule?
Which action configures the IEEE 802.1X Flexible Authentication feature to support Layer 3 authentication mechanisms?
Which Cisco security solution protects remote users against phishing attacks when they are not connected to
the VPN?
Which method must be used to connect Cisco Secure Workload to external orchestrators at a client site when the client does not allow incoming connections?
Which two products are used to forecast capacity needs accurately in real time? (Choose two.)
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements?
Which two methods are available in Cisco Secure Web Appliance to process client requests when configured in Transparent mode? (Choose two.)
An engineer is configuring Cisco Umbrella and has an identity that references two different policies. Which action ensures that the policy that the identity must use takes precedence over the second one?
Which Cisco product provides proactive endpoint protection and allows administrators to centrally manage the
deployment?
Which solution supports high availability in routed or transparent mode as well as in northbound and
southbound deployments?
An email administrator is setting up a new Cisco ESA. The administrator wants to enable the blocking of greymail for the end user. Which feature must the administrator enable first?
Using Cisco Cognitive Threat Analytics, which platform automatically blocks risky sites, and test unknown sites for hidden advanced threats before allowing users to click them?
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
What does Cisco ISE use to collect endpoint attributes that are used in profiling?
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client?
An administrator is adding a new Cisco ISE node to an existing deployment. What must be done to ensure that the addition of the node will be successful when inputting the FQDN?
What is the term for the concept of limiting communication between applications or containers on the same node?
Which Cisco command enables authentication, authorization, and accounting globally so that CoA is supported on the device?
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.

An engineer is configuring Cisco WSA and needs to deploy it in transparent mode. Which configuration component must be used to accomplish this goal?
Which VPN technology can support a multivendor environment and secure traffic between sites?
Which parameter is required when configuring a Netflow exporter on a Cisco Router?
Which risk is created when using an Internet browser to access cloud-based service?
Which Cisco Advanced Malware protection for Endpoints deployment architecture is designed to keep data
within a network perimeter?
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0380739941 address 0.0.0.0 command on hostA. The tunnel is not being established to hostB. What action is needed to authenticate the VPN?
Which API technology with SDN architecture is used to communicate with a controller and network devices such as routers and switches?
Which posture assessment requirement provides options to the client for remediation and requires the
remediation within a certain timeframe?
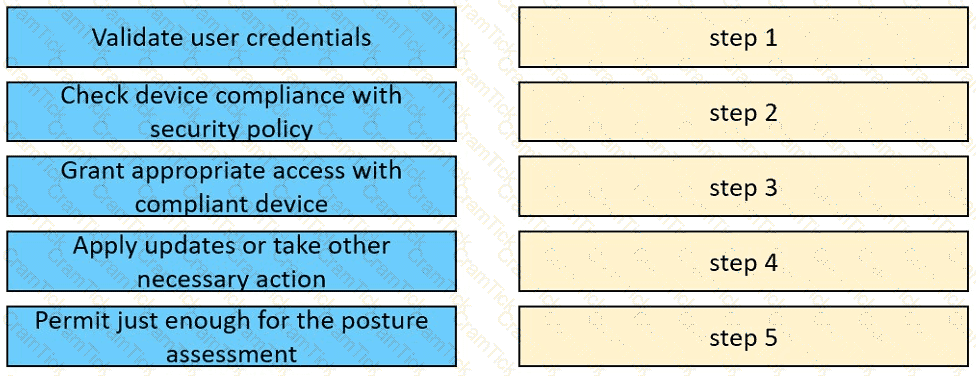
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
An organization is using DNS services for their network and want to help improve the security of the DNS infrastructure. Which action accomplishes this task?
Refer to the exhibit.

A network administrator configures command authorization for the admin5 user. What is the admin5 user able to do on HQ_Router after this configuration?
Which two capabilities of Integration APIs are utilized with Cisco Catalyst Center? (Choose two.)
Which action controls the amount of URI text that is stored in Cisco WSA logs files?
An engineer must configure AsyncOS for Cisco Secure Web Appliance to push log files to a syslog server using the SCP retrieval method. Drag and drop the steps from the left into the sequence on the right to complete the configuration.

A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access The Cisco ESA must also join a cluster machine using preshared keys What must be configured to meet these requirements?
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router. The organization
needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of
172.19.20.24. Which command on the hub will allow the administrator to accomplish this?
Which two protocols must be configured to authenticate end users to the Cisco WSA? (Choose two.)
What is the result of the ACME-Router(config)#login block-for 100 attempts 4 within 60 command on a Cisco IOS router?
Which Cisco security solution determines if an endpoint has the latest OS updates and patches installed on the system?
An organization has noticed an increase in malicious content downloads and wants to use Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web traffic. Which action will accomplish this task?
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the
corporate network. The endpoints must have the corporate antivirus application installed and be running the
latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the
network?
Which action configures the IEEE 802.1X Flexible Authentication feature lo support Layer 3 authentication mechanisms?
Which security solution uses NetFlow to provide visibility across the network, data center, branch offices, and cloud?
An administrator is trying to determine which applications are being used in the network but does not want the
network devices to send metadata to Cisco Firepower. Which feature should be used to accomplish this?
Which Cisco DNA Center RESTful PNP API adds and claims a device into a workflow?

Refer to the exhibit. An engineer must enable secure SSH protocols and enters this configuration. What are two results of running this set of commands on a Cisco router? (Choose two.)
Which attack type attempts to shut down a machine or network so that users are not able to access it?
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
An organization has two systems in their DMZ that have an unencrypted link between them for communication.
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability
would help an attacker brute force their way into the systems?
Email security has become a high priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (-10 00 to -6 00) on the Cisco ESA Which action will the system perform to disable any links in messages that match the filter?
What is an advantage of using a next-generation firewall compared to a traditional firewall?
Which solution is more secure than the traditional use of a username and password and encompasses at least two of the methods of authentication?
Based on the NIST 800-145 guide, which cloud architecture may be owned, managed, and operated by one or more of the organizations in the community, a third party, or some combination of them, and it may exist on or off premises?
Which two Cisco Umbrella security categories are used to prevent command-and-control callbacks on port 53 and protect users from being tricked into providing confidential information? (Choose two.)
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices. The default management
port conflicts with other communications on the network and must be changed. What must be done to ensure
that all devices can communicate together?
Which technology must De used to Implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
What is the purpose of the certificate signing request when adding a new certificate for a server?
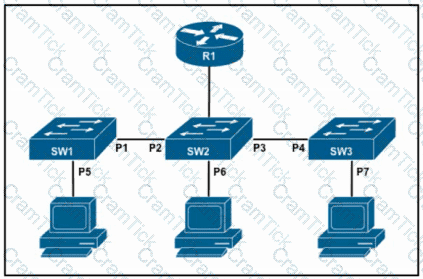
Refer to the exhibit. The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
Which two functions does the Cisco Advanced Phishing Protection solution perform in trying to protect from phishing attacks? (Choose two.)
An engineer is configuring Cisco WSA and needs to enable a separated email transfer flow from the Internet and from the LAN. Which deployment mode must be used to accomplish this goal?
An engineer is configuring IPsec VPN and needs an authentication protocol that is reliable and supports ACK
and sequence. Which protocol accomplishes this goal?
When Cisco and other industry organizations publish and inform users of known security findings and
vulnerabilities, which name is used?
Which type of API is being used when a controller within a software-defined network architecture dynamically
makes configuration changes on switches within the network?
An engineer needs a solution for TACACS+ authentication and authorization for device administration.
The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to
use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
Which two commands are required when configuring a flow-export action on a Cisco ASA? (Choose two.)
Which Cisco Secure Client module is integrated with Splunk Enterprise to provide monitoring capabilities to administrators to allow them to view endpoint application usage?
Which two methods must be used to add switches into the fabric so that administrators can control how switches are added into DCNM for private cloud management? (Choose two.)
Which security solution is used for posture assessment of the endpoints in a BYOD solution?
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing
authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details?
A networking team must harden an organization's network from VLAN hopping attacks. The team disables Dynamic Trunking Protocol and puts any unused ports in an unused VLAN. A trunk port is used as a trunk link. What must the team configure next to harden the network against VLAN hopping attacks?
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline
posture node?
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with
other cloud solutions via an API. Which solution should be used to accomplish this goal?
Which endpoint protection and detection feature performs correlation of telemetry, files, and intrusion
events that are flagged as possible active breaches?
Which telemetry data captures variations seen within the flow, such as the packets TTL, IP/TCP flags, and payload length?
An organization wants to implement a cloud-delivered and SaaS-based solution to provide visibility and threat detection across the AWS network. The solution must be deployed without software agents and rely on AWS VPC flow logs instead. Which solution meets these requirements?
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which
probe must be enabled for this type of profiling to work?
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed
through the Cisco Umbrella network. Which action tests the routing?
Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from
Cisco and other vendors to share data and interoperate with each other?
A network engineer is configuring a Cisco Catalyst switch. The network engineer must prevent traffic on the network from being interrupted by broadcast packets flooding the network using a predefined threshold. What must be configured on the switch?
Cisco SensorBase gaihers threat information from a variety of Cisco products and services and performs analytics to find patterns on threats Which term describes this process?
Refer to the exhibit.
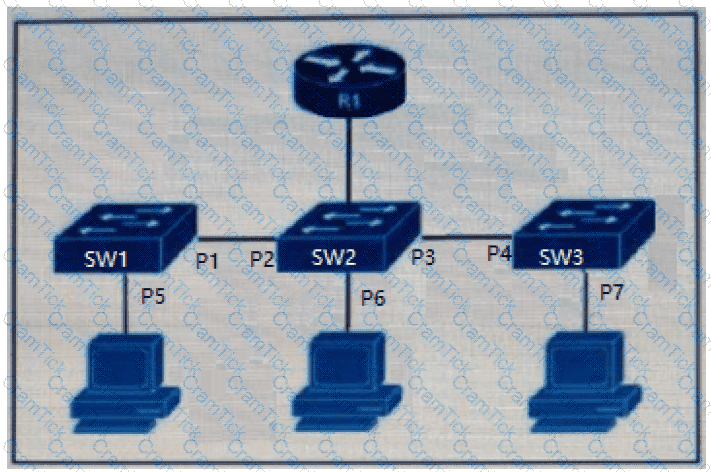
The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement?
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
Which direction do attackers encode data in DNS requests during exfiltration using DNS tunneling?
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
Drag and drop the cryptographic algorithms for IPsec from the left onto the cryptographic processes on the right.

Which DoS attack uses fragmented packets in an attempt to crash a target machine?
Which two types of connectors are used to generate telemetry data from IPFIX records in a Cisco Secure Workload implementation? (Choose two.)
What are two differences between a Cisco Secure Web Appliance that is running in transparent mode and one running in explicit mode? (Choose two.)
An organization has two machines hosting web applications. Machine 1 is vulnerable to SQL injection while machine 2 is vulnerable to buffer overflows. What action would allow the attacker to gain access to machine 1 but not machine 2?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites but other sites are not accessible due to an error. Why is the error occurring?
Which characteristic is unique to a Cisco WSAv as compared to a physical appliance?
A security engineer must add destinations into a destination list in Cisco Umbrella. What describes the application of these changes?
What is the term for having information about threats and threat actors that helps mitigate harmful events that would otherwise compromise networks or systems?
What provides total management for mobile and PC including managing inventory and device tracking, remote view, and live troubleshooting using the included native remote desktop support?
Which open source tool does Cisco use to create graphical visualizations of network telemetry on Cisco IOS XE devices?
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.)
An organization has a requirement to collect full metadata information about the traffic going through their AWS cloud services They want to use this information for behavior analytics and statistics Which two actions must be taken to implement this requirement? (Choose two.)
A network engineer has configured a NTP server on a Cisco ASA. The Cisco ASA has IP reachability to the
NTP server and is not filtering any traffic. The show ntp association detail command indicates that the
configured NTP server is unsynchronized and has a stratum of 16. What is the cause of this issue?
How many interfaces per bridge group does an ASA bridge group deployment support?
An engineer is configuring Dropbox integration with Cisco Cloudlock. Which action must be taken before granting API access in the Dropbox admin console?
An administrator is adding a new switch onto the network and has configured AAA for network access control. When testing the configuration, the RADIUS authenticates to Cisco ISE but is being rejected. Why is the ip radius source-interface command needed for this configuration?
Which component of Cisco umbrella architecture increases reliability of the service?
An organization recently installed a Cisco WSA and would like to take advantage of the AVC engine to allow the organization to create a policy to control application specific activity. After enabling the AVC engine, what must be done to implement this?
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two)
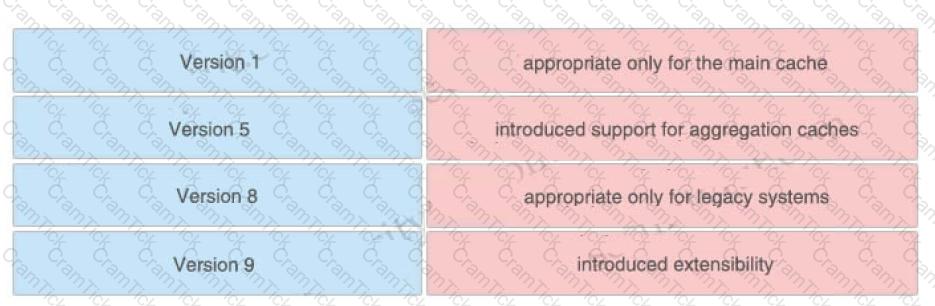
Drag and drop the descriptions from the left onto the correct protocol versions on the right.
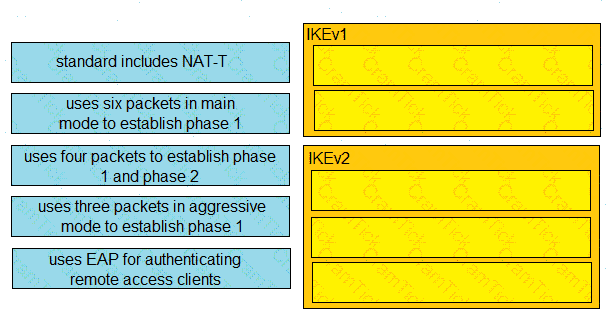
Drag and drop the deployment models from the left onto the explanations on the right.

What are two ways that Cisco Container Platform provides value to customers who utilize cloud service providers? (Choose two.)
Which Cisco ISE service checks the compliance of endpoints before allowing the endpoints to connect to
the network?
What is the recommendation in a zero-trust model before granting access to corporate applications and
resources?
A network engineer must configure a Cisco Secure Email Gateway to prompt users to enter two forms of information before gaining access. The Secure Email Gateway must also join a cluster machine using preshared keys. What must be configured to meet these requirements?
An engineer is implementing Cisco CES in an existing Microsoft Office 365 environment and must route inbound email to Cisco CE.. record must be modified to accomplish this task?
What is the recommendation in a zero-trust model before granting access to corporate applications and resources?
A Cisco AMP for Endpoints administrator configures a custom detection policy to add specific MD5 signatures The configuration is created in the simple detection policy section, but it does not work What is the reason for this failure?
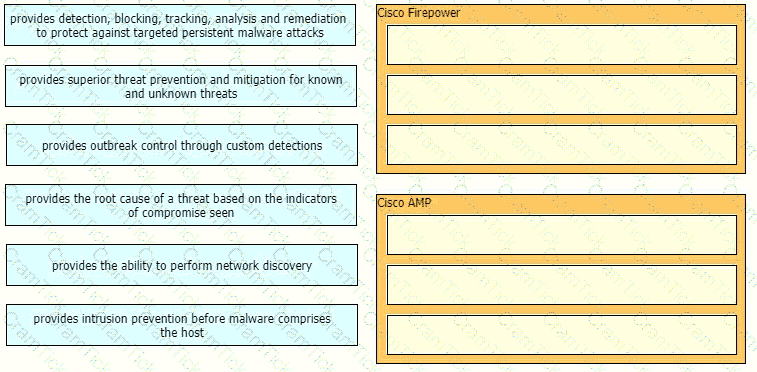
Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right.
Which two request of REST API are valid on the Cisco ASA Platform? (Choose two)
Which two protocols must be configured to authenticate end users to the Web Security Appliance? (Choose two.)
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
An engineer adds a custom detection policy to a Cisco AMP deployment and encounters issues with the
configuration. The simple detection mechanism is configured, but the dashboard indicates that the hash is not 64 characters and is non-zero. What is the issue?
Which VMware platform does Cisco ACI integrate with to provide enhanced visibility, provide policy integration and deployment, and implement security policies with access lists?
An organization must add new firewalls to its infrastructure and wants to use Cisco ASA or Cisco FTD.
The chosen firewalls must provide methods of blocking traffic that include offering the user the option to bypass the block for certain sites after displaying a warning page and to reset the connection. Which solution should the organization choose?
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains IPs, and flies, and helps to pinpoint attackers' infrastructures and predict future threat?
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social
engineering attacks? (Choose two)
Which Cisco ISE feature helps to detect missing patches and helps with remediation?
Which configuration method provides the options to prevent physical and virtual endpoint devices that are in the same base EPG or uSeg from being able to communicate with each other with Vmware VDS or Microsoft vSwitch?
Which two request methods of REST API are valid on the Cisco ASA Platform? (Choose two.)
Drag and drop the common security threats from the left onto the definitions on the right.

Using Cisco Firepower’s Security Intelligence policies, upon which two criteria is Firepower block based?
(Choose two)
Refer to the exhibit.

Which configuration item makes it possible to have the AAA session on the network?
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments?
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
Which two solutions help combat social engineering and phishing at the endpoint level? (Choose two.)
What is a difference between a zone-based firewall and a Cisco Adaptive Security Appliance firewall?
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two)
In which cloud services model is the customer responsible for scanning for and mitigation of application vulnerabilities?
Why is it important for the organization to have an endpoint patching strategy?
An organization is receiving SPAM emails from a known malicious domain. What must be configured in order to
prevent the session during the initial TCP communication?
Which two behavioral patterns characterize a ping of death attack? (Choose two)
Which CLI command is used to register a Cisco FirePower sensor to Firepower Management Center?
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256
cisc0380739941 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
Which Cisco solution integrates industry-leading artificial intelligence and machine learning analytics and an assurance database to review the security posture and maintain visibility of an organization’s cloud environment?
An engineer is implementing DHCP security mechanisms and needs the ability to add additional attributes to profiles that are created within Cisco ISE Which action accomplishes this task?
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443. The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users. What must be done on the Cisco WSA to support these requirements?
CCNP Security | 350-701 Written Exam | 350-701 Questions Answers | 350-701 Test Prep | 350-701 CCNP Security Actual Questions | Implementing and Operating Cisco Security Core Technologies (SCOR) Exam Questions PDF | 350-701 Online Exam | 350-701 Practice Test | 350-701 PDF | 350-701 CCNP Security Dumps | 350-701 Test Questions | 350-701 Study Material | 350-701 Exam Preparation | 350-701 Valid Dumps | 350-701 Real Questions | 350-701 CCNP Security Practice Test | CCNP Security 350-701 Dumps | Implementing and Operating Cisco Security Core Technologies (SCOR) Exam Questions


