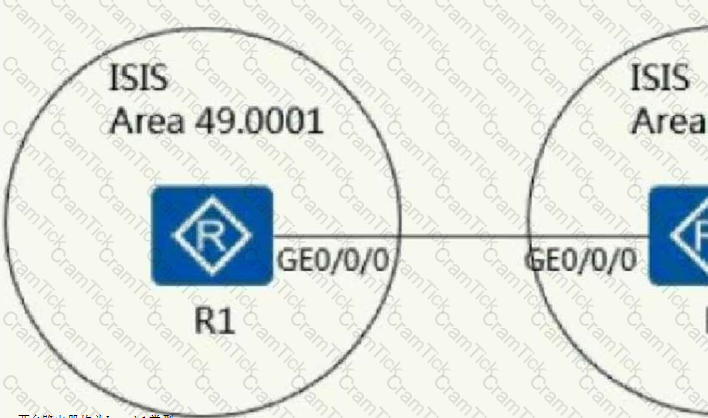
As shown in the figure, which of the following options can satisfy two routers to establish an ISIS neighbor relationship?
Regarding the authentication of the ISIS protocol, the correct statement is:(multiple choice)
When the BFD detection time intervals at both ends are 30ms and 40ms respectively. Which of the following options is correct?
in MPLS-In the case of IBGP-VPN, if only BGP and LDP are used to distribute labels, the MPLS labels of packets can be up to two layers of labels.
Which of the following statements about MUX VLAN are correct? (Multiple choices)
BGP4+ is running between the two routers, and the neighbor relationship is normal, but the BGP routing table of the local router does not have any neighbor routing entries. The following possible reasons are:
Between two directly connected devices that have established IBBP neighbors, run the shutdown command to shut down the interface of one of the devices, and the BGP connection will not be disconnected immediately.
For the description of the firewall security zone, which of the following statements is correct? (single choice)
Which of the following regular expressions can match only the BGP routing entries that pass through AS200 and then through AS300?
OSPIn Fv3, the Router-LSA is generated for each router, which describes the interface address and cost of each link of the router, and also includes the RouterID of the neighboring router.
If the network runs the OSPF protocol, configure the non-backbone area in the OSPF area as Totaly After the stub area, ABThe R router will send Totally An L is delivered to the stub areas Id 0.0.0.0 LSA, which type of LSA does this LSA belong to??
SSH uses asymmetric encryption algorithms AES and DES to realize the security of data transmission, and uses HMAC to ensure the security of data transmission.
Integrity check for data integrity
In order to enable the VPN instance to advertise IP routes to the BGP-EVPN address family, what command needs to be enabled in the BGP view
The two routers are connected together through serial ports, but they cannot ping each other. Now check the port status as follows:
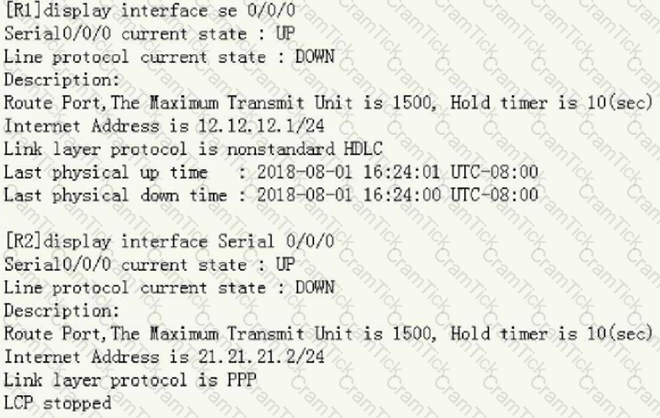
Can you determine the cause from the above information?
If there are multiple receivers in a multicast group, the administrator enables IGM on the switch connecting the receiversP Snooping function, when the receiver changes from
When the switch receives the general group query message from the querier, how should multiple receivers respond?
After dividing an interface of the firewall into the Untrust security zone, the interface belongs to the untrust zone and no longer belongs to the Local zone.
When deploying BGP/MPLS IP VPN, the OSPF VPN Route Tag (VPN Route Tag) is not transmitted in the extended community attribute of MP-BGP, it is only a local concept, and only the PE that receives the MP-BGP route and generates OSPF LSA Makes sense on the router.
The MAC address table of the switch with default configuration is empty at this time, and the host A connected to the switch sends the first unicast data frame, then what operation will the switch perform after receiving the instruction?
Both OSPFv3 and ISIS are running on the router, and OSPFv3 routes need to be imported into ISIS. Which of the following import configurations is correct: (Multiple Choice)
How many interfaces of the router have IS-IS enabled, the output is as follows:

The following descriptions about routing policies and policy routing are correct:
There is an As-path-filter: ip as-path-filter 1 permit .*(100|400)$, the As-path-filter Can not. Which of the following AS_PATH attributes match?
in cross-domain VPN_Option During packet forwarding in mode B, two ASBsR needs to exchange the public and LSP labels once.
Two routers, connected together through serial ports, However, the interconnection cannot be pinged. Now check the port status as follows
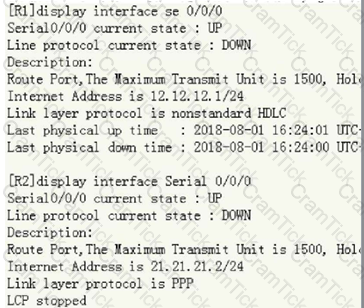
Can you identify the cause from the above information? (Single Choice)
Regarding the description of the security level of the firewall security zone, what is wrong?
The host HW1 in the HW device network wants to join a video conference, what will the host do?
When the stateless address configuration method is used to configure the IPv4 of the host6 address, and viaDHCPv6 get in addition toHow to set the M and 0 bits in the RA message when there are other parameters other than the address?
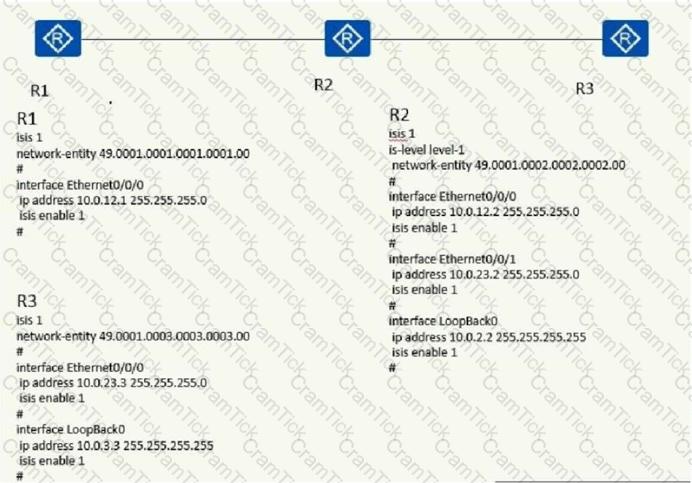
The topology diagram and configuration are as follows. Now I hope that there is no detailed routing entry for 10.0.3.3/32 in the R1 routing table. The following statement can achieve this requirementhave
The HTTP protocol is based on TCP, so TCP can be used Flood attack defense method defends HTTP Flood attack.
In the process of viewing the debug output through the SSH terminal, a lot of information pops up. Which of the following operations can make the monitor terminal no longer pop up the debug message?
When running 0SPFv3 on a Huawei router, the OSPFv3 process will automatically select an interface address as the
for the processRouter ID.
As shown in the figure, the MP-BGP neighbor relationship is established between PE1 and PE2 through the Loopback0 interface. After the configuration is completed, it is found that CE1 and CE2 cannot learn routes from each other. Which of the following options will cause this problem?

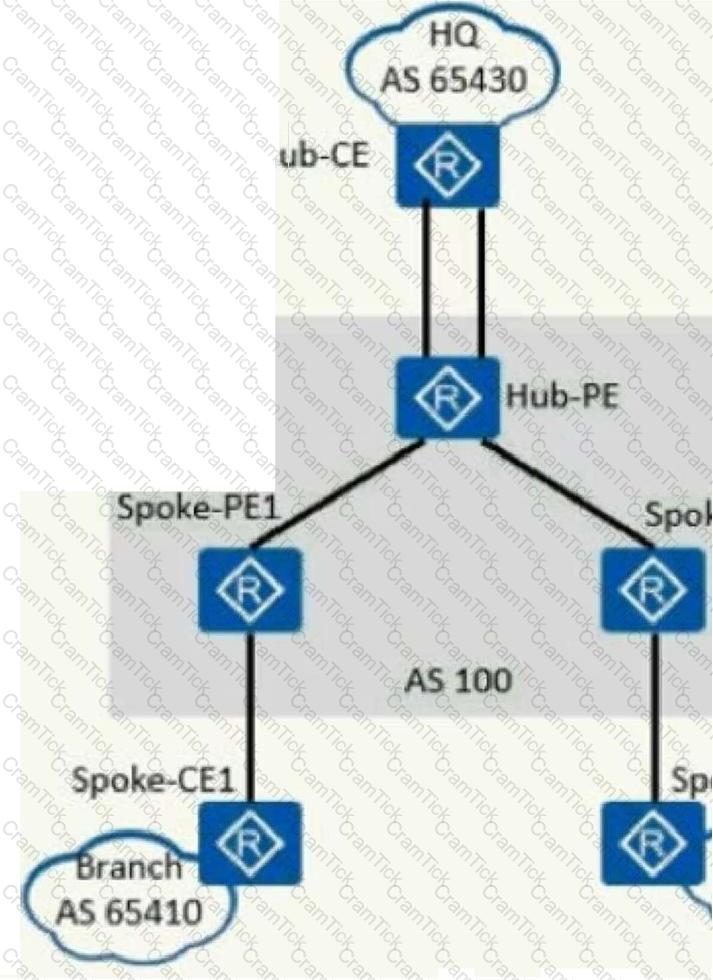
As shown in the figure, an enterprise hopes to realize the secure mutual access between the head office and each branch through MPLS/VPN, and requires that the VPN traffic of the branches must be forwarded through the head office to monitor the traffic. Which of the options described in this solution is wrong?
There is a new HW office that needs to use their router as a DHCP server. When configuring the DHCP server to provide DHCP service for the HW office, which of the following items need to be configured?
Which of the following statements about the tail of ISIS protocol LSP packets is correct?
the following aboutThe establishment process of LDP LSP, which description is correct?
If the advertised route entry is deleted on the BGP router, the BGP router will be triggered to send an Update message for route revocation. Well-known mandatory attribute with revoked routing entries.
ISIS Elections in Broadcast Multiple Access NetworkDIS, which of the following statements about DIS is correct?
If the interface sticky MAC function is enabled, what is the number of MAC addresses learned by the interface by default?
OSPRouter in F Lin included in LSAk What are the types of Type? (Multiple Choice)
As shown below,R1 and R2 have established a Level 2 neighbor relationship. The key configuration is as follows. The following statement about the routing entry of R2 is correct

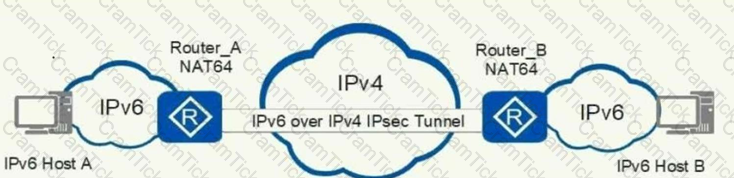
As shown in the figure, there are two IPv6 networks that can access the IPv4 network. At the same time, an IPSec tunnel needs to be established between the two IPv6 networks for communication.Which of the following packaging modes can meet the above requirements?
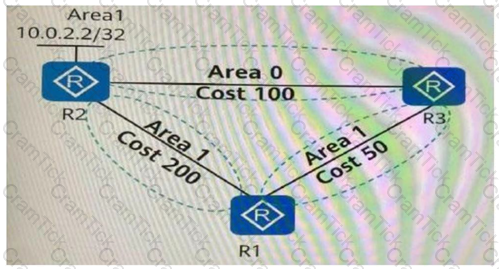
As shown in the figure, OSPF is enabled on all interfaces of the router, and. The cost value is indicated in the figure, and the Loopback0 interface of R2 is advertised in the area 1, thenR1 arrives 10. 0.2.2/32Cost value?
Which of the following LSAs are only spread within a single area? (multiple choice)
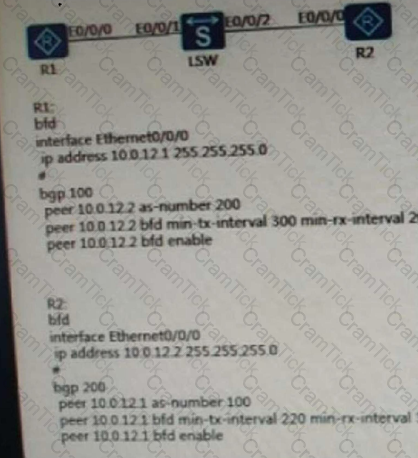
As shown below, R1 and R2 establish EBGP neighbors and enable the BFD detection function. Which of the following statements is correct (single choice)
The intranet users of a company use the no-pat mode of NAT to access the Internet. If all the public network IP addresses are used, what will happen to the intranet users who access the Internet subsequently?
BGP4+ carries the next-hop address of the IPv6 route through the next-Hop attribute in the Update packet.
Which of the following statements about the format of OSPFv3 packets is correct?? (multiple choice)
Routing & Switching | H12-261_V3.0 Questions Answers | H12-261_V3.0 Test Prep | HCIE-Routing & Switching (Written) V3.0 Questions PDF | H12-261_V3.0 Online Exam | H12-261_V3.0 Practice Test | H12-261_V3.0 PDF | H12-261_V3.0 Test Questions | H12-261_V3.0 Study Material | H12-261_V3.0 Exam Preparation | H12-261_V3.0 Valid Dumps | H12-261_V3.0 Real Questions | Routing & Switching H12-261_V3.0 Exam Questions