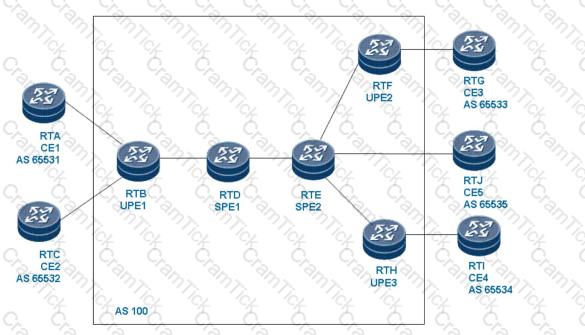
Refer to the exhibit
 .
.
As shown in the figure, basic BGP/MPLS IP VPN configuration has been completed on routers. Which of the following configurations is incorrect for advertising default
routes in VPN instances on the SPE?
Note: All configurations are performed on the SPE.
According to the inter-AS VPN Option A, which protocol is used to forward traffic between ASBRs?
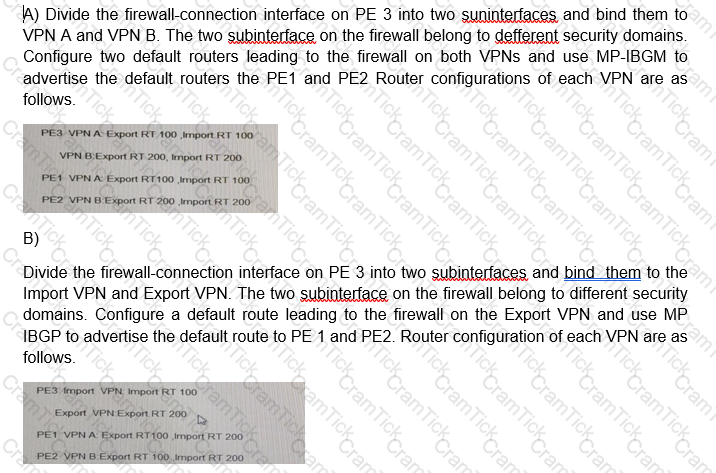
On the IP bearer network, different VPN users (VPN A and VPN B) must access the internet through the same egress. Which of the following schemes can achieve security isolation VPNs and have the best scalability?

Configure VRFs and relevant policies on a PE as follows:
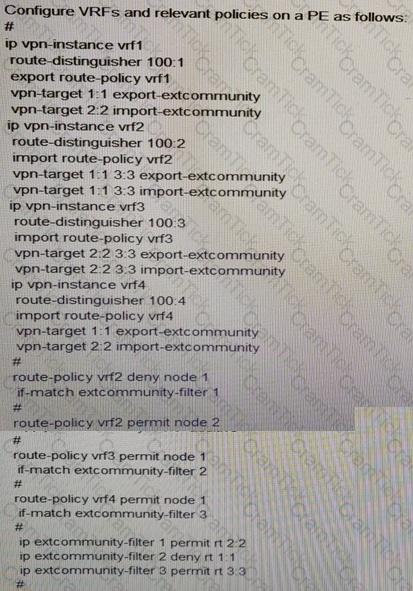
If a route is imported to the routing table of VRF 1, which VRF can the route match?
multicast routing-enable
#
acl number 2000
rule 5 permit source 225.0.0.0 0.0.0.255
#
interface Ethernet6/1/0
ip address 10.1.1.1 255.255.255.0
igmp enable
pim sm
#
igmp
#
pim
ssm-policy 2000
#
return
The preceding are partial multicast router configurations. Which of the following configurations
are required to configure the SSM Mapping on Ethernet 6/1/0 and map IGMPv2 Report messages for multicast group 225.0.0.1 to multicast source 2.2.2.2?
The VRRP is enabled on the firewall dual-system Intranet users use NAT to access extranet FTP services Which of the following statements are true?
In PIM-DM, which of the following scenarios about sending Join messages is true?
On the IP bearer network, which of the following methods can be used to manage devices on the backbone network and switches on the signaling VPN?
As shown in the figure, RTA, RTB, RTC are interconnected over IS-IS, RTA,
RTD, RTE, and RTC are interconnected over OSPF. Both IS-IS and OSPF use the default costs. RSVPTE is enabled on all routers and the interfaces between these routers. The Loopback0 interface of RTC is 192.168.0.3/32 and is advertised in both OSPF and ISIS areas. 192.168.0.3/32 is also the LSR ID of MPLS. Configurations of the MPLS and tunnel on RTA:
#
mpls lsr-id 192.168.0.1
mpls
mpls te
mpls rsvp-te
mpls te cspf
interface Tunnel1/0/0
tunnel-protocol mpls te
destination 192.168.0.3
mpls te tunnel-id 1
mpls te path metric-type igp
mpls te igp metric absolute 1
mpls te commit
#
Which path will be selected when the tunnel becomes Up? What is the metric of this tunnel?
In the access architecture of an IP bearer network, the OSPF protocol is enabled between two access routers, two firewalls (in transparent mode), and two Layer 3 switches. Softswitches work in active/standby mode. VRRP is enabled between the softswitches to provide a gateway. In normalcases, SW1 is the master router and SW2 is the backup router. Considering the reliability of the access network, how would you plan the cost value of each link in the OSPF area?
The inner VLAN tag in layer 2 user packets is used to differentiated key services from other services. If packets are not processed after being encapsulated by QinQ, the 802. 1p information of the inner VLAN tag becomes invalid. After the QinQ is employed, three methods can be used to configure conditions for sensing 8021p configuration of the inner VLAN tag:
1. Reset the 802.1p of the outer VLAN tag regardless of the existing 02 1p configurations of the inner VLAN tag.
2. Automatically swap the 802. 1p configurations of the inner VLAN tag to that of the outer VLAN tag.
3. Reset the 802.1p configurations of the outer VLAN tag based on the existing 802.1p configurations of the different VLAN tags
Which of the following statements about TE FRR in forwarding adjacency (FA) mode and TE FRR in IGP Shortcut mode are true?
#
interface Ethernet6/1/1
ip address 40.1.1.4 255.255.255.0
igmp prompt-leaveigmp enable
pim sm
#
IGMP interface group report information of VPN-Instance: public net
Ethernet6/1/1(40.1.1.4):
Total 1 IGMP Group reported
Group: 224.1.2.3
Uptime: 00:00:32
Expires: 00:04:38
Last reporter: 30.1.1.30
Last-member-query-counter: 0
Last-member-query-timer-expiry: off
Version1-host-present-timer-expiry: off
The preceding information shows the configurations of Ethernet 6/1/1 and entries created based on received IGMPv2 Report messages. Which action does Ethernet 6/1/1 perform after receiving Leave messages for group 224.1.2.3?
Which statement describes the delay requirement of the voice service for the IP bearer network?
As shown in the figure, the bearer network is deployed in full mesh mode. For example, RTA uses the physical interface ATM 1/0/0. The interface is devised into ATM 10/0.2 connect to RTC and RTD, respectively . The GigabiteEthernet 2/0/0 and GigabitEthernet 3/0/0 interface are used to set up a trunk as the VRRP heartbeat cable. The UMG work in active/standby mode. Media interface connected to RTA and RTB belong to VLAN 10. VRRP is enable at the VLAN interface RTA is the master router. The interface is configured as follows:

Which of the following RTA configurations are correct in VLAN 10?
A)
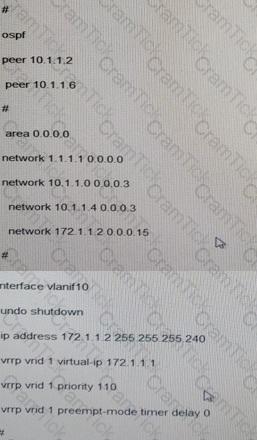
B)
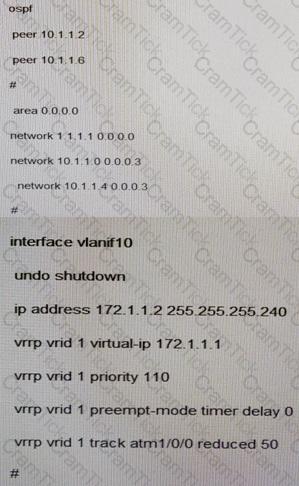
C)
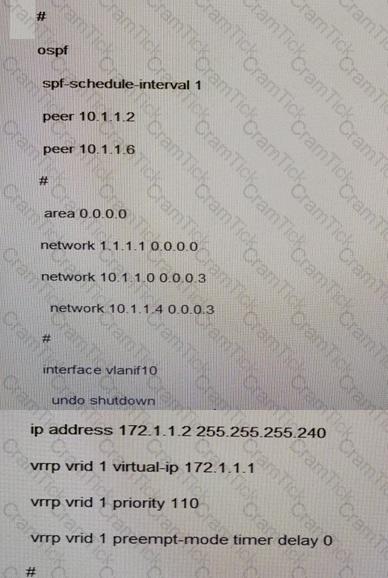
D)
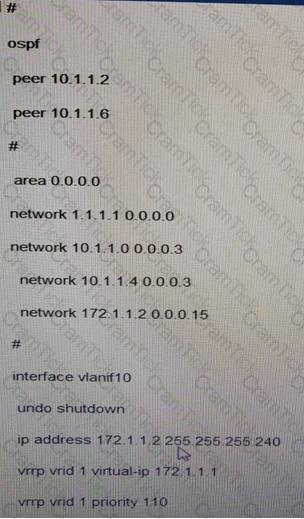
Which of the following are conditions for bringing the remote CCC connection Up? (ABE)
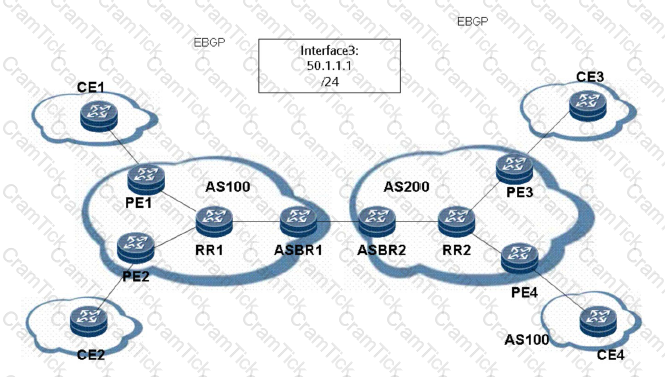
As shown in the figure, the AS number of operator 1 is 100 and that of
operator 2 is 200. Option C is used for exchanging VPN routes between AS 100 and AS 200. Which of the following statements about Option C are true?
Refer to the exhibit.
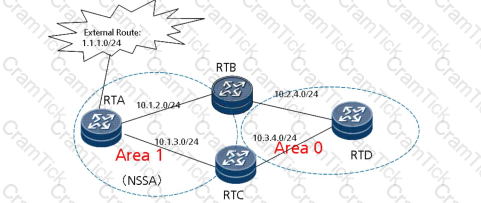
As shown in the figure, RT 5 is a stub area router, an external Internet route is imported by RT 1, and a virtual connection is established between RT 1 and RT 3.At present, the Internet is accessible to routers except RT 5. Why can the Internet not be accessed from RT 5?(Select two answers)
Which of the following statements about the working principle f LDAP FRR are true?
HCIE-Carrier IP | H31-161 Questions Answers | H31-161 Test Prep | HCIE-Carrier IP (Written) Questions PDF | H31-161 Online Exam | H31-161 Practice Test | H31-161 PDF | H31-161 Test Questions | H31-161 Study Material | H31-161 Exam Preparation | H31-161 Valid Dumps | H31-161 Real Questions | HCIE-Carrier IP H31-161 Exam Questions