You must setup a Ddos solution for your ISP. The solution must be agile and not block legitimate traffic.
Which two products will accomplish this task? (Choose two.)
You are asked to determine if the 203.0.113.5 IP address has been added to the third-party security feed, DS hield, from Juniper Seclnte1. You have an SRX Series device that is using Seclnte1 feeds from Juniper ATP Cloud
Which command will return this information?
Exhibit
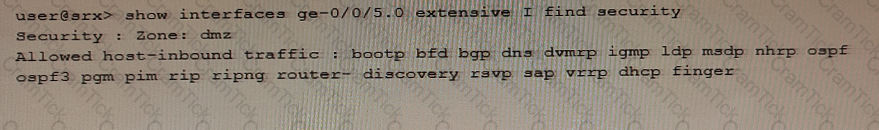
Referring to the exhibit, which three protocols will be allowed on the ge-0/0/5.0 interface? (Choose three.)
To analyze and detect malware, Juniper ATP Cloud performs which two functions? (Choose two.)
You want to enforce I DP policies on HTTP traffic.
In this scenario, which two actions must be performed on your SRX Series device? (Choose two )
Exhibit.
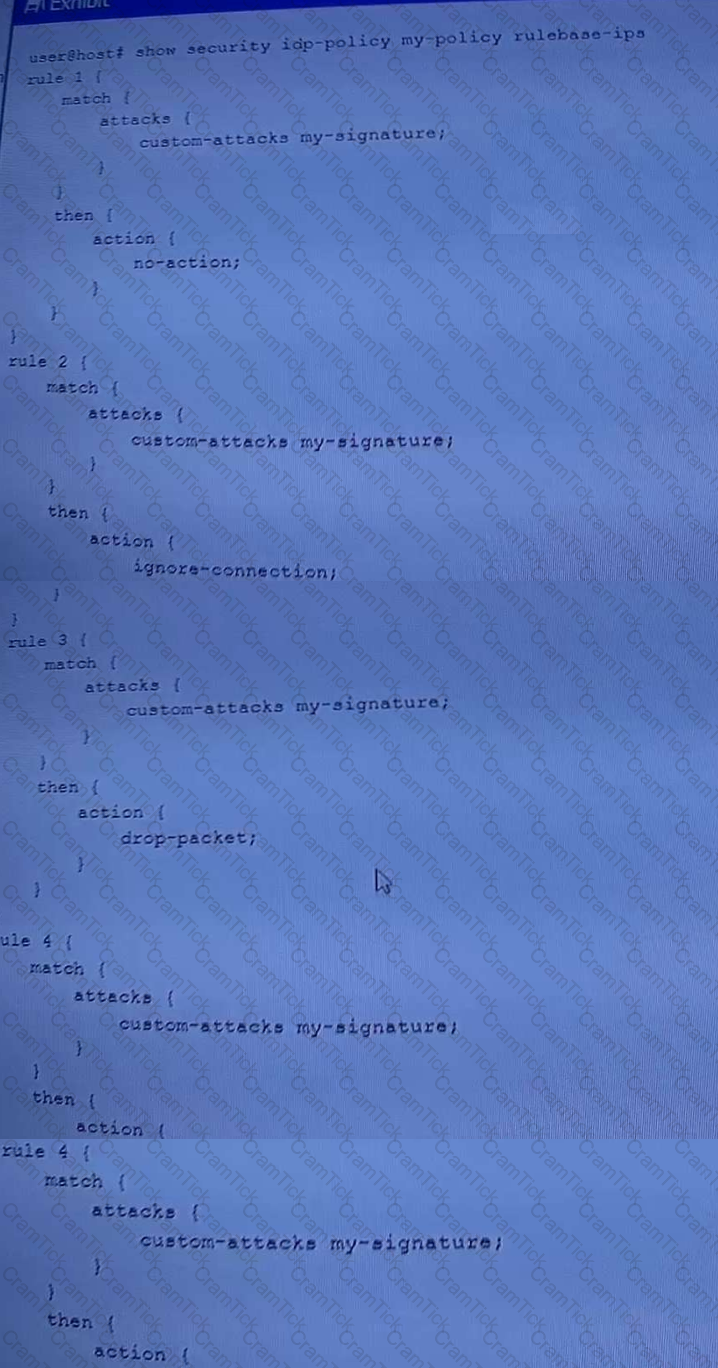
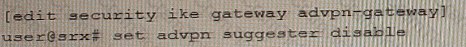
A hub member of an ADVPN is not functioning correctly.
Referring the exhibit, which action should you take to solve the problem?
Your organization has multiple Active Directory domain to control user access. You must ensure that security polices are passing traffic based upon the user’s access rights.
What would you use to assist your SRX series devices to accomplish this task?
Your Source NAT implementation uses an address pool that contains multiple IPv4 addresses Your users report that when they establish more than one session with an external application, they are prompted to authenticate multiple times External hosts must not be able to establish sessions with internal network hosts
What will solve this problem?
Which method does an SRX Series device in transparent mode use to learn about unknown devices in a network?
Exhibit
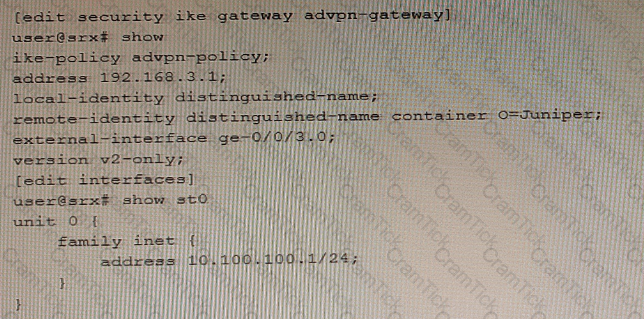
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
A)
B)
C)

D)

You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restricted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
A)
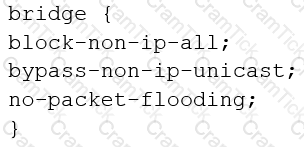
B)
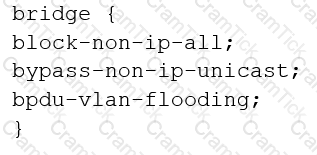
C)
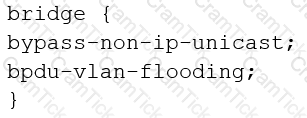
D)

Exhibit
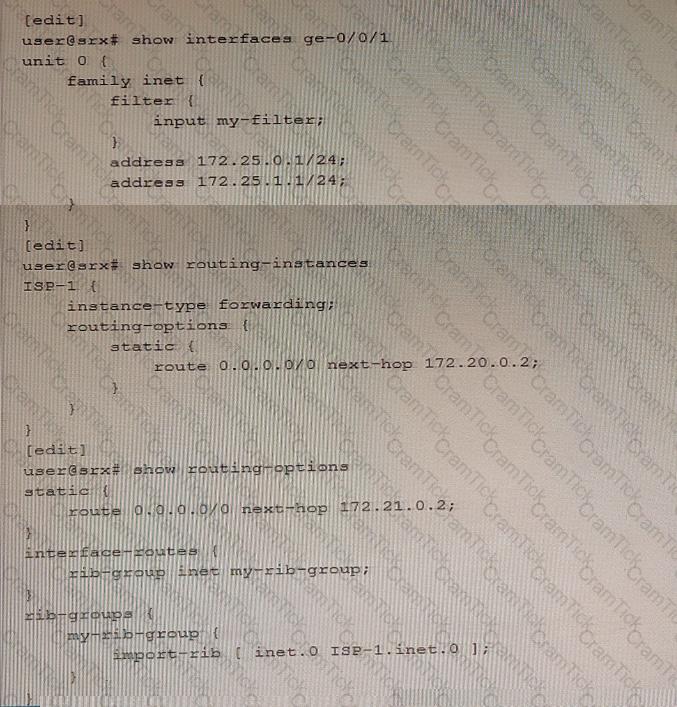
You are implementing filter-based forwarding to send traffic from the 172.25.0.0/24 network through ISP-1 while sending all other traffic through your connection to ISP-2. Your ge-0/0/1 interface connects to two networks, including the 172.25.0.0/24 network. You have implemented the configuration shown in the exhibit. The traffic from the 172.25.0.0/24 network is being forwarded as expected to 172.20.0.2, however traffic from the other network (172.25.1.0/24) is not being forwarded to the upstream 172.21.0.2 neighbor.
In this scenario, which action will solve this problem?
You are asked to share threat intelligence from your environment with third party tools so that those
tools can be identify and block lateral threat propagation from compromised hosts.
Which two steps accomplish this goal? (Choose Two)
Which two statements are correct regarding tenant systems on SRX Series devices? (Choose two.)
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario? (Choose two.)
What are two important function of the Juniper Networks ATP appliance solution? (Choose two.).
In Juniper ATP Cloud, what are two different actions available in a threat prevention policy to deal with an infected host? (Choose two.)
your company wants to take your juniper ATP appliance into private mode. You must give them a list
of impacted features for this request.
Which two features are impacted in this scenario? (Choose two)
You are required to deploy a security policy on an SRX Series device that blocks all known Tor network IP addresses. Which two steps will fulfill this requirement? (Choose two.)
you configured a security policy permitting traffic from the trust zone to the untrust zone but your
traffic not hitting the policy.
In this scenario, which cli command allows you to troubleshoot traffic problem using the match criteria?
Exhibit
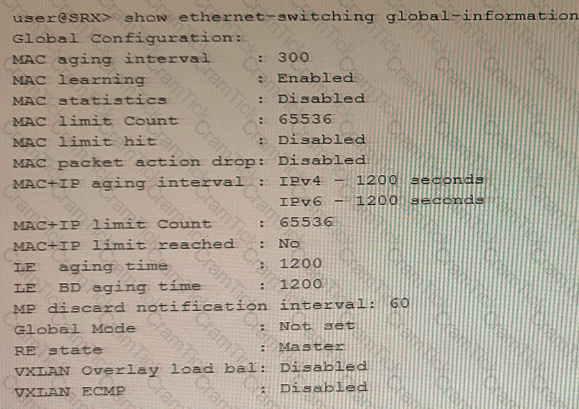
You have configured the SRX Series device to switch packets for multiple directly connected hosts that are within the same broadcast domain However, the traffic between two hosts in the same broadcast domain are not matching any security policies
Referring to the exhibit, what should you do to solve this problem?
You are required to secure a network against malware. You must ensure that in the event that a
compromised host is identified within the network. In this scenario after a threat has been
identified, which two components are responsible for enforcing MAC-level infected host ?
Your company uses non-Juniper firewalls and you are asked to provide a Juniper solution for zero-day malware protection. Which solution would work in this scenario?
Exhibit
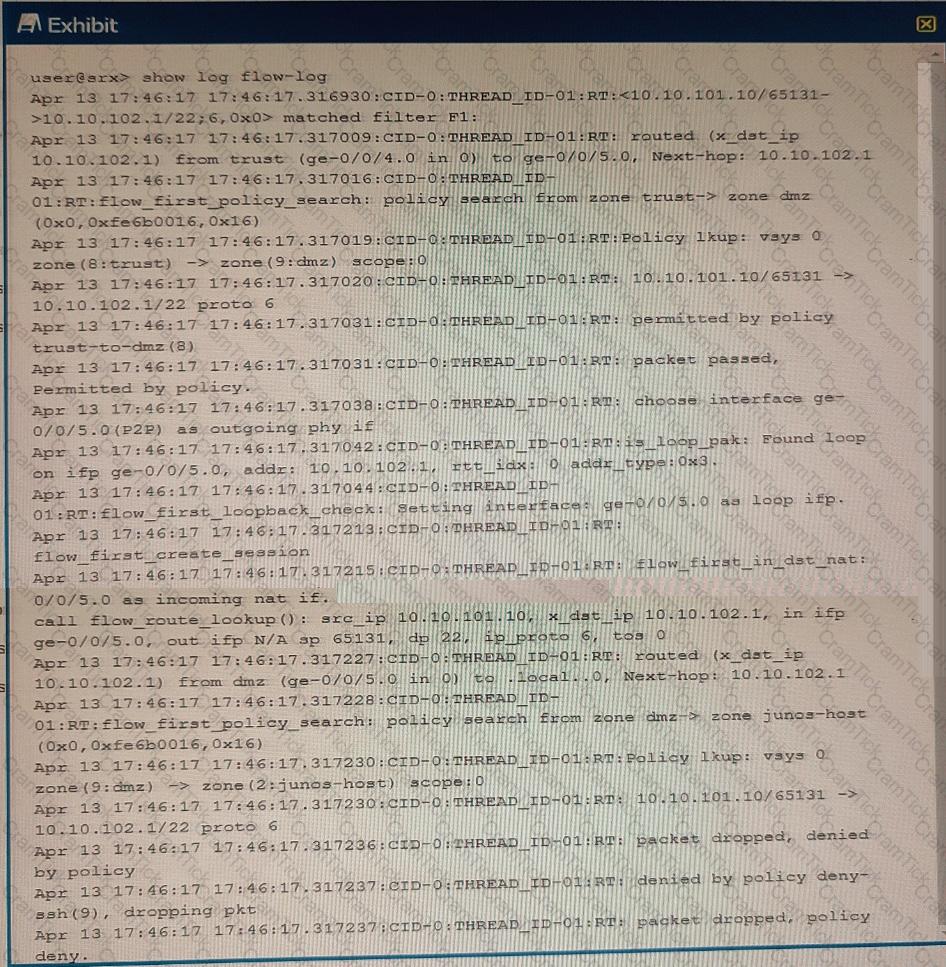
Referring to the exhibit, which three statements are true? (Choose three.)
You opened a support ticket with JTAC for your Juniper ATP appliance. JTAC asks you to set up access to the device
using the reverse SSH connection.Which three setting must be configured to satisfy this request? (Choose three.)


