You discover the ongoing use of the native Dropbox client in your organization. Although Dropbox is not a corporate-approved application, you do not want to prevent the use of Dropbox. You do, however, want to ensure visibility into its usage.
You are provisioning Netskope users from Okta with SCIM Provisioning, and users are not showing up in the tenant. In this scenario, which two Netskope components should you verify first In Okta for accuracy? (Choose two.)
You want to allow both the user identities and groups to be imported in the Netskope platform. Which two methods would satisfy this requirement? (Choose two.)
Your customer has some managed Windows-based endpoints where they cannot add any clients or agents. For their users to have secure access to their SaaS application, you suggest that the customer use Netskope's Explicit Proxy.
Which two configurations are supported for this use case? (Choose two.)
You want to prevent a document stored in Google Drive from being shared externally with a public link. What would you configure in Netskope to satisfy this requirement?
You want to provision users and groups to a Netskope tenant. You have Microsoft Active Directory servers hosted in two different forests. Which statement is true about this scenario?
Review the exhibit.
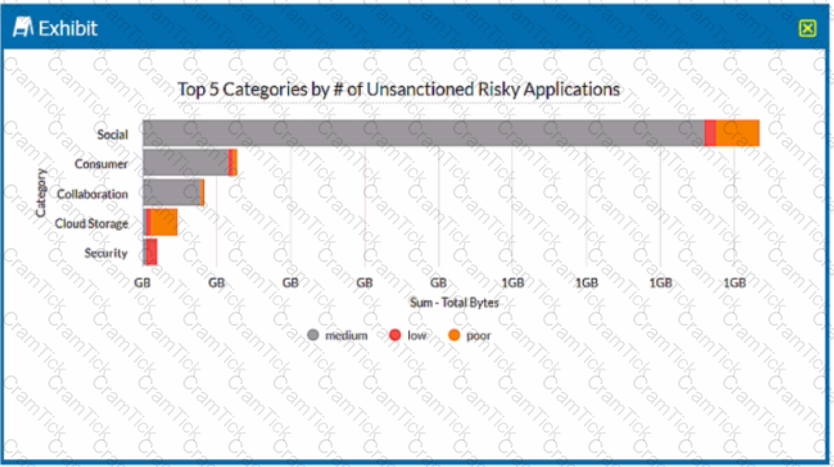
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)
Review the exhibit.
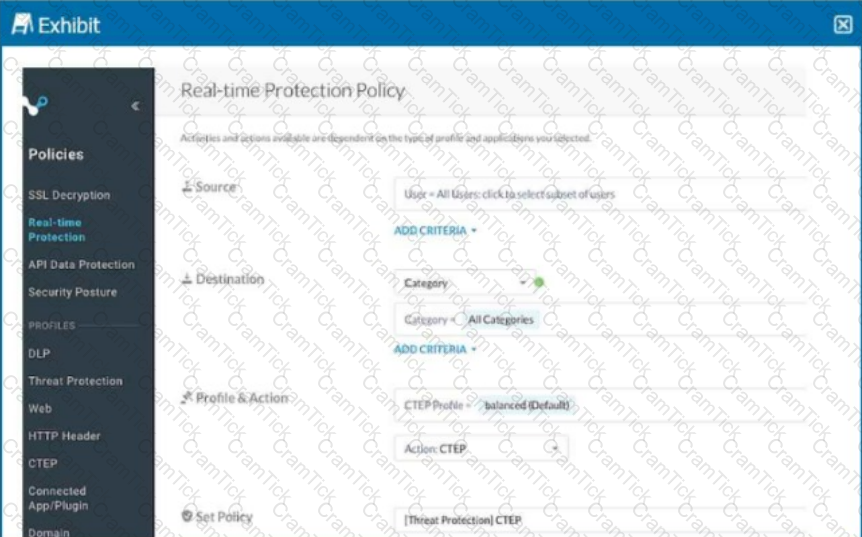
Your Real-time Protection policy contains some rules with only a browse activity. The exhibit shows a new policy rule.
Where is the correct location to place this rule?
The director of IT asks for confirmation If your organization's Web traffic would be blocked when the Netskope client fails. In this situation, what would confirm the fail close status?
After deploying the Netskope client to a number of devices, users report that the Client status indicates "Admin Disabled". User and gateway information is displayed correctly in the client configuration dialog
Why are clients installing in an "Admin Disabled" state in this scenario?
You are troubleshooting an issue with Microsoft where some users complain about an issue accessing OneDrive and SharePoint Online. The configuration has the Netskope client deployed and active for most users, but some Linux machines are routed to Netskope using GRE tunnels. You need to disable inspection for all users to begin troubleshooting the issue.
In this scenario, how would you accomplish this task?
To which three event types does Netskope's REST API v2 provide access? (Choose three.)
The risk team at your company has determined that traffic from the sales team to a custom Web application should not be inspected by Netskope. All other traffic to the Web application should continue to be inspected. In this scenario, how would you accomplish this task?
You are using the Netskope DLP solution. You notice flies containing test data for credit cards are not triggering DLP events when uploaded to Dropbox. There are corresponding page events. Which two scenarios would cause this behavior? (Choose two.)
Review the exhibit.
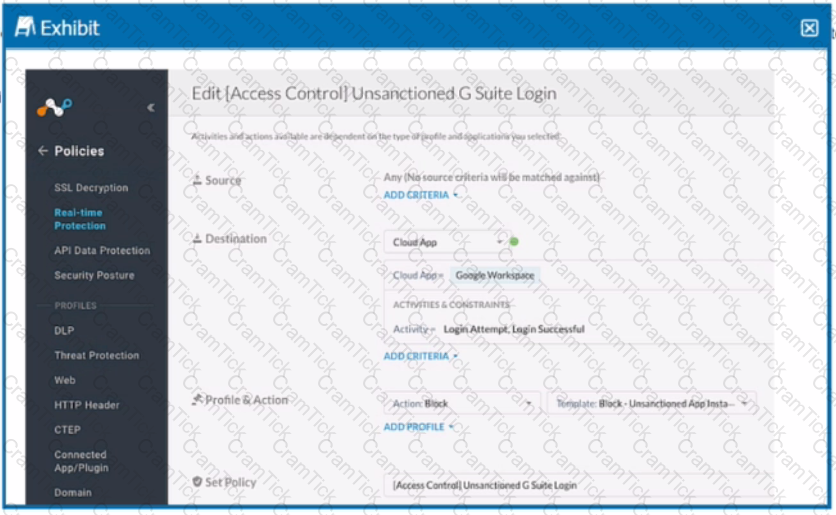
Your company uses Google as the corporate collaboration suite; however, corporate policy restricts the use of personal Google services. The exhibit provides a partially completed policy to ensure that users cannot log into their personal account.
What should be added to achieve the desired outcome in this scenario?
You have deployed Netskope Secure Web Gateway (SWG). Users are accessing new URLs that need to be allowed on a daily basis. As an SWG administrator, you are spending a lot of time updating Web policies. You want to automate this process without having to log into the Netskope tenant
Which solution would accomplish this task?
Review the exhibit.
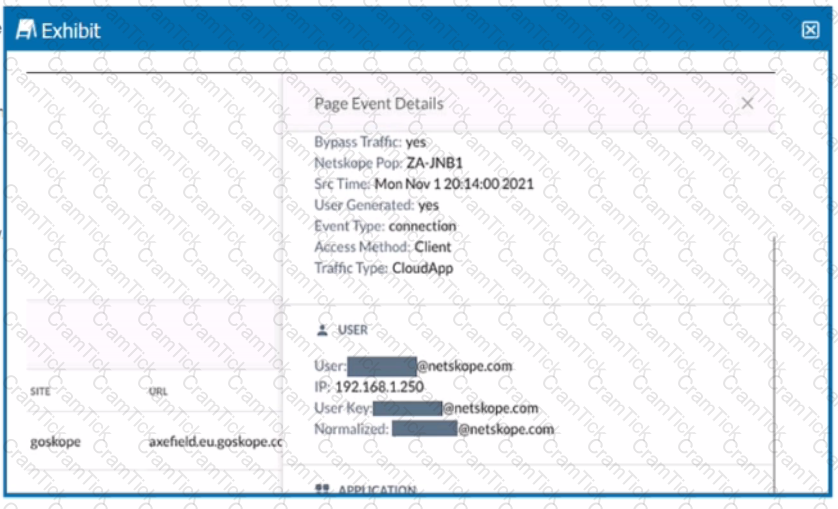
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
Your company wants to deploy Netskope using a tunnel because you have a mixture of device operating systems. You also do not want to enable encryption because you want to maximize bandwidth.
Your company has a Symantec BlueCoat proxy on-premises and you want to deploy Netskope using proxy chaining. Which two prerequisites need to be enabled first in this scenario? (Choose two.)
Review the exhibit.
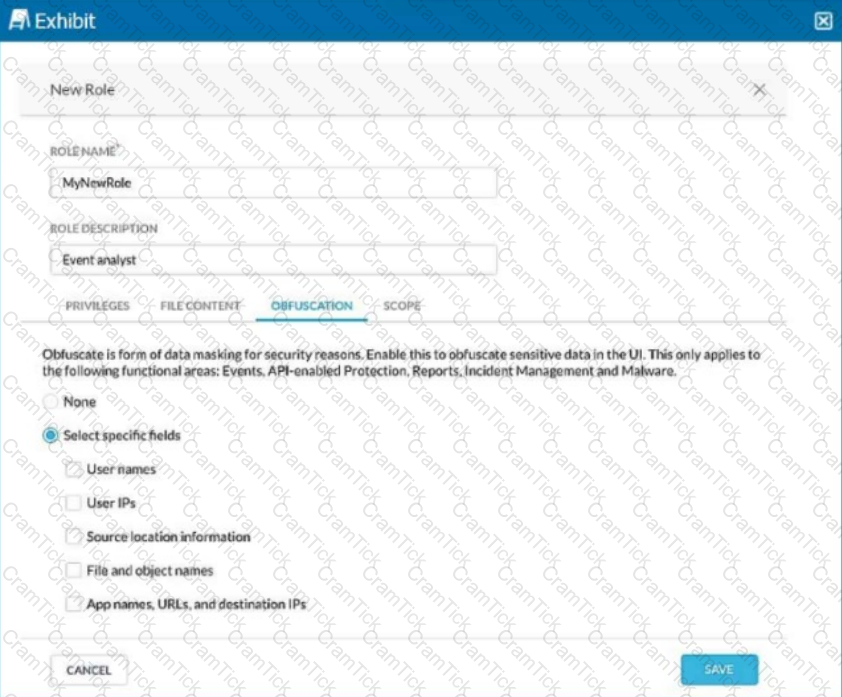
You are asked to create a new role that allows analysts to view Events and Reports while providing user privacy. You need to avoid directly exposing identities and user location information.
Which three fields must you obfuscate in this scenario? (Choose three.)
Your customer currently only allows users to access the corporate instance of OneDrive using SSO with the Netskope client. The users are not permitted to take their laptops when vacationing, but sometimes they must have access to documents on OneDrive when there is an urgent request. The customer wants to allow employees to remotely access OneDrive from unmanaged devices while enforcing DLP controls to prohibit downloading sensitive files to unmanaged devices.
Which steering method would satisfy the requirements for this scenario?
You are using the Netskope DLP solution. You notice that valid credit card numbers in a file that you just uploaded to an unsanctioned cloud storage solution are not triggering a policy violation. You can see the Skope IT application events for this traffic but no DLP alerts.
Which statement is correct in this scenario?
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as Crowdstrike.
Which two requirements are needed for a successful integration and sharing of threat data? (Choose two.)
NCCSI |


