A senior security engineer flags the following log file snippet as having likely facilitated an attacker’s lateral movement in a recent breach:
qry_source: 19.27.214.22 TCP/53
qry_dest: 199.105.22.13 TCP/53
qry_type: AXFR
| in comptia.org
------------ directoryserver1 A 10.80.8.10
------------directoryserver2 A 10.80.8.11
------------ directoryserver3 A 10.80.8.12
------------ internal-dns A 10.80.9.1
----------- www-int A 10.80.9.3
------------ fshare A 10.80.9.4
------------ sip A 10.80.9.5
------------ msn-crit-apcs A 10.81.22.33
Which of the following solutions, if implemented, would mitigate the risk of this issue reoccurring?
After an organization met with its ISAC, the organization decided to test the resiliency of its security controls against a small number of advanced threat actors. Which of the following will enable the security administrator to accomplish this task?
A company is preparing to move a new version of a web application to production. No issues were reported during security scanning or quality assurance in the CI/CD pipeline. Which of the following actions should thecompany take next?
Protected company data was recently exfiltrated. The SOC did not find any indication of a network or outside physical intrusion, and the DLP systems reported no unusual activity. The incident response team determined a text file was encrypted and reviews the following log excerpt:

Which of the following is the most appropriate action for the team to take?
A network security architect for an organization with a highly remote workforce implements an always-on VPN to meet business requirements. Which of the following best explains why the architect is using this approach?
A global company’s Chief Financial Officer (CFO) receives a phone call from someone claiming to be the Chief Executive Officer (CEO). The caller claims to be stranded and in desperate need of money. The CFO is suspicious, but the caller’s voice sounds similar to the CEO’s. Which of the following best describes this type of attack?
A financial technology firm works collaboratively with business partners in the industry to share threat intelligence within a central platform This collaboration gives partner organizations the ability to obtain and share data associated with emerging threats from a variety of adversaries Which of the following should the organization most likely leverage to facilitate this activity? (Select two).
After an incident occurred, a team reported during the lessons-learned review that the team.
* Lost important Information for further analysis.
* Did not utilize the chain of communication
* Did not follow the right steps for a proper response
Which of the following solutions is the best way to address these findinds?
A security architect is investigating instances of employees who had their phones stolen in public places through seemingly targeted attacks. Devices are able to access company resources such as email and internal documentation, some of which can persist in application storage. Which of the following would best protect the company from information exposure? (Select two).
An incident response analyst finds the following content inside of a log file that was collected from a compromised server:
.2308464678 ... whoami ..... su2032829%72%322/// ...... /etc/passwd .... 2087031731467478432 ...
$6490/90/./ ..< XML ?.. .... nty.
Which of the following is the best action to prevent future compromise?
A security administrator needs to review the efficacy of the detection rules configured on the SIEM by employing real-world attacker TTPs. Which of the following actions should the security administrator take to accomplish this objective?
An organization wants to implement a platform to better identify which specific assets are affected by a given vulnerability. Which of the following components provides the best foundation to achieve this goal?
A security engineer reviews an after action report from a previous security breach and notes a long lag time between detection and containment of a compromised account. The engineer suggests using SOAR to address this concern. Which of the following best explains the engineer's goal?
An organization recently implemented a purchasing freeze that has impacted endpoint life-cycle management efforts. Which of the following should a security manager do to reduce risk without replacing the endpoints?
During DAST scanning, applications are consistently reporting code defects in open-source libraries that were used to build web applications. Most of the code defects are from using libraries with known vulnerabilities. The code defects are causing product deployment delays. Which of the following is the best way to uncover these issues earlier in the life cycle?
An organization recently acquired another company that is running a different EDR solution. A SOC analyst wants to automate the isolation of endpoints that are found to be compromised. Which of the following workflows best mitigates the risk of false positives and reduces the spread of malicious code?
Which of the following best describes the challenges associated with widespread adoption of homomorphic encryption techniques?
An organization currently has IDS, firewall, and DLP systems in place. The systems administrator needs to integrate the tools in the environment to reduce response time. Which of the following should the administrator use?
A security engineer must resolve a vulnerability in a deprecated version of Python for a custom-developed flight simul-ation application that is monitored and controlled remotely. The source code is proprietary and built with Python functions running on the Ubuntu operating system. Version control is not enabled for the application in development or production. However, the application must remain online in the production environment using built-in features. Which of the following solutions best reduces theattack surface of these issues and meets the outlined requirements?
Which of the following best explains the importance of determining organization risk appetite when operating with a constrained budget?
A security engineer receives an alert from the SIEM platform indicating a possible malicious action on the internal network. The engineer generates a report that outputs the logs associated with the incident:

Which of the following actions best enables the engineer to investigate further?
PKI can be used to support security requirements in the change management process. Which of the following capabilities does PKI provide for messages?
A company receives reports about misconfigurations and vulnerabilities in a third-party hardware device that is part of its released products. Which of the following solutions is the best way for the company to identify possible issues at an earlier stage?

An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simul-ation, please click the Reset All button.
Based on the results of a SAST report on a legacy application, a security engineer is reviewing the following snippet of code flagged as vulnerable:
Which of the following is the vulnerable line of code that must be changed?

An organization mat performs real-time financial processing is implementing a new backup solution Given the following business requirements?
* The backup solution must reduce the risk for potential backup compromise
* The backup solution must be resilient to a ransomware attack.
* The time to restore from backups is less important than the backup data integrity
* Multiple copies of production data must be maintained
Which of the following backup strategies best meets these requirement?
A compliance officer is reviewing the data sovereignty laws in several countries where the organization has no presence Which of the following is the most likely reason for reviewing these laws?
A company updates itscloud-based services by saving infrastructure code in a remote repository. The code is automatically deployed into the development environment every time the code is saved lo the repository The developers express concern that the deployment often fails, citing minor code issues and occasional security control check failures in the development environment Which of the following should a security engineer recommend to reduce the deployment failures? (Select two).
An organization is developing a disaster recovery plan that requires data to be backed up and available at a moment's notice. Which of the following should the organization consider first to address this requirement?
An organization is looking for gaps in its detection capabilities based on the APTs that may target the industry Which of the following should the security analyst use to perform threatmodeling?
A company is having issues with its vulnerability management program New devices/lPs are added and dropped regularly, making the vulnerability report inconsistent Which of the following actions should the company lake to most likely improve the vulnerability management process'
A security engineer receives the following findings from a recent security audit:
• Data should be protected based on user permissions and roles.
• User action tracking should be implemented across the network.
• Digital identities should be validated across the data access workflow.
Which of the following is the first action the engineer should take to address the findings?
Which of the following AI concerns is most adequately addressed by input sanitation?
A compliance officer isfacilitating abusiness impact analysis (BIA)and wantsbusiness unit leadersto collect meaningful data. Several business unit leaders want more information about the types of data the officer needs.
Which of the following data types would be the most beneficial for the compliance officer?(Select two)
A security analyst is reviewingsuspicious log-in activity and sees the following data in the SICM:

Which of the following is the most appropriate action for the analyst to take?
A systems administrator wants to reduce the number of failed patch deployments in an organization. The administrator discovers that system owners modify systems or applications in an ad hoc manner. Which of the following is the best way to reduce the number of failed patch deployments?
A company recentlyexperienced aransomware attack. Although the company performssystems and data backupon a schedule that aligns with itsRPO (Recovery Point Objective) requirements, thebackup administratorcould not recovercritical systems and datafrom its offline backups to meet the RPO. Eventually, the systems and data were restored with information that wassix months outside of RPO requirements.
Which of the following actions should the company take to reduce the risk of a similar attack?
A company's SICM Is continuously reporting false positives and false negatives The security operations team has Implemented configuration changes to troubleshoot possible reporting errors Which of the following sources of information best supports the required analysts process? (Select two).
An organization is increasing its focus on training that addresses new social engineering and phishing attacks. Which of the following is the organization most concerned about?
A company SIEM collects information about the log sources. Given the following report information:

Which of the following actions should a security engineer take to enhance the security monitoring posture?
A security analyst is reviewing a SIEM and generates the following report:

Later, the incident response team notices an attack was executed on the VM001 host. Which of the following should the security analyst do to enhance the alerting process on the SIEM platform?
A manufacturing plant is updating its IT services. During discussions, the senior management team created the following list of considerations:
• Staff turnover is high and seasonal.
• Extreme conditions often damage endpoints.
• Losses from downtime must be minimized.
• Regulatory data retention requirements exist.
Which of the following best addresses the considerations?
Recent repents indicate that a software tool is being exploited Attackers were able to bypass user access controls and load a database. A security analyst needs to find the vulnerability and recommend a mitigation. The analyst generates the following output:

Which of the following would the analyst most likely recommend?
A company lined an email service provider called my-email.com to deliver company emails. The company stalled having several issues during the migration. A security engineer is troubleshooting and observes the following configuration snippet:

Which of the following should the security engineer modify to fix the issue? (Select two).
An organization is deploying a new data lake that will centralize records from several applications. During the design phase, the security architect identifies the following requirements:
• The sensitivity levels of the data is different.
• The data must be accessed through stateless API calls after authentication.
• Different users will have access to different data sets.
Which of the following should the architect implement to best meet these requirements?
A vulnerability scan was performed on a website, and the following encryption suites were found:

Which of the following actions will remediate the vulnerability?
A security operations analyst is reviewing network traffic baselines for nightly database backups. Given the following information:

Which of the following should the security analyst do next?
A company that uses containers to run its applications is required to identify vulnerabilities on every container image in a private repository The security team needs to be able to quickly evaluate whether to respond to a given vulnerability Which of the following, will allow the security team to achieve the objective with the last effort?
A building camera is remotely accessed and disabled from the remote console application during off-hours. A security analyst reviews the following logs:

Which of the following actions should the analyst take to best mitigate the threat?
An organization is developing on Al-enabled digital worker to help employees complete common tasks such as template development, editing, research, and scheduling. As part of the Al workload the organization wants to Implement guardrails within the platform. Which of the following should the company do to secure the Al environment?
A systems engineer is configuring SSO for a business that will be using SaaS applications for its remote-only workforce. Privileged actions in SaaS applications must be allowed only from corporate mobile devices that meet minimum security requirements, but BYOD must also be permitted for other activity. Which of the following would best meet this objective?
An administrator reviews the following log and determines the root cause of a site-to-site tunnel failure:

Which of the following actions should the administrator take to most effectively correct the failure?
A security analyst is performing threat modeling for a new AI chatbot. The AI chatbot will be rolled out to help customers develop configuration information within the company's SaaS offering. Which of the following issues would require involvement from the company's internal legal team?
A security operations engineer needs to prevent inadvertent data disclosure when encrypted SSDs are reused within an enterprise. Which of the following is the most secure way to achieve this goal?
A company receives several complaints from customers regarding its website. An engineer implements a parser for the web server logs that generates the following output:

which of the following should the company implement to best resolve the issue?
An analyst wants to conduct a risk assessment on a new application that is being deployed. Given the following information:
• Total budget allocation for the new application is unavailable.
• Recovery time objectives have not been set.
• Downtime loss calculations cannot be provided.
Which of the following statements describes the reason a qualitative assessment is the best option?
A security engineer wants to enhance the security posture of end-user systems in a Zero Trust environment. Given the following requirements:
. Reduce the ability for potentially compromised endpoints to contact command-and-control infrastructure.
. Track the requests that the malware makes to the IPs.
. Avoid the download of additional payloads.
Which of the following should the engineer deploy to meet these requirements?
A nation-state actor is exposed for attacking large corporations by establishing persistence in smaller companies that are likely to be acquired by these large corporations. The actor then provisions user accounts in the companies for use post-acquisition. Before an upcoming acquisition, a security officer conducts threat modeling with this attack vector. Which of the following practices is the best way to investigate this threat?
A security manager at a local hospital wants to secure patient medical records. The manager needs to:
• Choose an access control model that clearly defines who has access to sensitive information.
• Prevent those who enter new patient information from specifying who has access to this data.
Which of the following access control models is the best way to ensure the lowest risk of granting unintentional access?
A security engineer needs to remediate a SWEET32 vulnerability in an OpenSSH-based application and review existing configurations. Which of the following should the security engineer do? (Select two.)
A security analyst isreviewing the following event timeline from an COR solution:

Which of the following most likely has occurred and needs to be fixed?
A security analyst received a report that an internal web page is down after a company-wide update to the web browser Given the following error message:

Which of the following is the b«« way to fix this issue?
A software development team requires valid data for internal tests. Company regulations, however do not allow the use of this data in cleartext. Which of the following solutions best meet these requirements?
A company wants to modify its process to comply with privacy requirements after an incident involving PII data in a development environment. In order to perform functionality tests, the QA team still needs to use valid data in the specified format. Which of the following best addresses the risk without impacting the development life cycle?
Which of the following best describes a common use case for homomorphic encryption?
An engineering team determines the cost to mitigate certain risks is higher than the asset values The team must ensure the risks are prioritized appropriately. Which of the following is the best way to address the issue?
Employees use their badges to track the number of hours they work. The badge readers cannot be upgraded due to facility constraints. The software for the badge readers uses a legacy platform and requires connectivity to the enterprise resource planning solution. Which of the following is the best to ensure the security of the badge readers?
An organization wants to create a threat model to identity vulnerabilities in its infrastructure. Which of the following, should be prioritized first?
A systems administrator works with engineers to process and address vulnerabilities as a result of continuous scanning activities. The primary challenge faced by the administrator is differentiating between valid and invalid findings. Which of the following would the systems administrator most likely verify is properly configured?
After discovering that an employee is using a personal laptop to access highly confidential data, a systems administrator must secure the company's data. Which of the following capabilities best addresses this situation?
A company detects suspicious activity associated with external connections Security detection tools are unable tocategorize this activity. Which of the following is the best solution to help the company overcome this challenge?
An auditor is reviewing the logs from a web application to determine the source of an incident. The web application architecture includes an internet-accessible application load balancer, a number of web servers in a private subnet, application servers, and one database server in a tiered configuration. The application load balancer cannot store the logs. The following are sample log snippets:
Web server logs:
192.168.1.10 - - [24/Oct/2020 11:24:34 +05:00] "GET /bin/bash" HTTP/1.1" 200 453 Safari/536.36
192.168.1.10 - - [24/Oct/2020 11:24:35 +05:00] "GET / HTTP/1.1" 200 453 Safari/536.36
Application server logs:
24/Oct/2020 11:24:34 +05:00 - 192.168.2.11 - request does not match a known local user. Querying DB
24/Oct/2020 11:24:35 +05:00 - 192.168.2.12 - root path. Begin processing
Database server logs:
24/Oct/2020 11:24:34 +05:00 [Warning] 'option read_buffer_size1 unassigned value 0 adjusted to 2048
24/Oct/2020 11:24:35 +05:00 [Warning] CA certificate ca.pem is self-signed.
Which of the following should the auditor recommend to ensure future incidents can be traced back to the sources?
An attacker infiltrated the code base of a hardware manufacturer and inserted malware before the code was compiled. The malicious code is now running at the hardware level across a number of industries and sectors. Which of the following categories best describes this type of vendor risk?
A global company with a remote workforce implemented a new VPN solution. After deploying the VPN solution to several hundred users, the help desk starts receiving reports of slow access to both internally and externally available applications. A security analyst reviews the following:
VPN client routing: 0.0.0.0/0 → eth1
Which of the following solutions should the analyst use to fix this issue?
During a gap assessment, an organization notes that OYOD usage is asignificant risk. The organization implemented administrative policies prohibiting BYOD usage However, the organization has not implemented technical controls to prevent the unauthorized use of BYOD assets when accessing the organization's resources. Which of the following solutions should the organization implement to b»« reduce the risk of OYOD devices? (Select two).
A company sells a security appliance assembled from globally sourced hardware and software components. Installing the security appliance requires enabling administrative permissions for the service accounts on the appliance. Which of the following allows the company to reassure new and existing customers that the risk introduced by the appliance is minimal?
A software engineer is creating a CI/CD pipeline to support the development of a web application The DevSecOps team is required to identify syntax errors Which of the following is the most relevant to the DevSecOps team's task'
A Chief Information Security Officer (CISO) is concerned that a company's current data disposal procedures could result in data remanence. The company uses only SSDs. Which of the following would be the most secure way to dispose of the SSDs given the CISO's concern?
A user reports application access issues to the help desk. The help desk reviews the logs for the user:

Which of the following is most likely the reason for the issue?
A company reduced its staff 60 days ago, and applications are now starting to fail. The security analyst is investigating to determine if there is malicious intent for the application failures. The security analyst reviews the following logs:
22:03:50 sshd[21502]: Success login for user01 from 192.168.2.5
22:10:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:11:40 sshd[21502]: Success login for user07 from 192.168.2.58
22:12:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:13:00 sshd[21502]: Failed login for user10 from 192.168.2.5
22:13:00 sshd[21502]: Success login for user03 from 192.168.2.27
22:13:00 sshd[21502]: Failed login for user10 from 192.168.2.5
Which of the following is the most likely reason for the application failures?
A user reports application access issues to the help desk. The help desk reviews the logs for the user

Which of the following is most likely The reason for the issue?
An analyst reviews a SIEM and generates the following report:

OnlyHOST002is authorized for internet traffic. Which of the following statements is accurate?
A security architect is mitigating a vulnerability that previously led to a web application data breach. An analysis into the root cause of the issue finds the following:
An administrator’s account was hijacked and used on several Autonomous System Numbers within 30 minutes.
All administrators use named accounts that require multifactor authentication.
Single sign-on is used for all company applications.Which of the following should the security architect do to mitigate the issue?
All organization is concerned about insider threats from employees who have individual access to encrypted material. Which of the following techniques best addresses this issue?
A global organization wants to manage all endpoint and user telemetry. The organization also needs to differentiate this data based on which office it is correlated to. Which of the following strategies best aligns with this goal?
An ISAC supplied recent threat intelligence information about pictures used on social media that provide reconnaissance of systems in use in secure facilities. In response, the Chief Information Security Officer (CISO) wants several configuration changes implemented via the MDM to ensure the following:
• Camera functions and location services are blocked for corporate mobile devices.
• All social media is blocked on the corporate and guest wireless networks.
Which of the following is the CISO practicing to safeguard against the threat?
During a vulnerability assessment, a scan reveals the following finding:
Windows Server 2016 Missing hotfix KB87728 - CVSS 3.1 Score: 8.1 [High] - Affected host 172.16.15.2
Later in the review process, the remediation team marks the finding as a false positive. Which of the following is the best way toavoid this issue on future scans?

An administrator needs to craft a single certificate-signing request for a web-server certificate. The server should be able to use the following identities to mutually authenticate other resources over TLS:
• wwwJnt.comptia.org
• webserver01.int.comptia.org
•10.5.100.10
Which of the following certificate fields must be set properly to support this objective?
A company needs to quickly assess whether software deployed across the company's global corporate network contains specific software libraries. Which of the following best enables the company's SOC to respond quickly when such an assessment is required?
A security analyst is reviewing the following authentication logs:
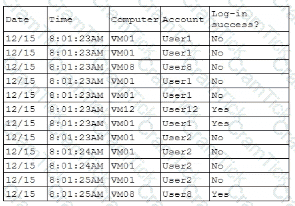
Which of the following should the analyst do first?
A security analyst is reviewing the following vulnerability assessment report:
192.168.1.5, Host = Server1, CVSS 7.5, Web Server, Remotely Executable = Yes, Exploit = Yes
205.1.3.5, Host = Server2, CVSS 6.5, Bind Server, Remotely Executable = Yes, Exploit = POC
207.1.5.7, Host = Server3, CVSS 5.5, Email Server, Remotely Executable = Yes, Exploit = Yes
192.168.1.6, Host = Server4, CVSS 9.8, Domain Controller, Remotely Executable = Yes, Exploit = Yes
Which of the following should be patched first to minimize attacks against internet-facing hosts?


