A static code analysis report of a web application can be leveraged to identify:
Which of the following BEST describes the difference between a red team engagement and a penetration test?
A penetration tester is required to exploit a WPS implementation weakness. Which of the following tools will perform the attack?
A penetration testing company was hired to conduct a penetration test against Company A's network of 20.10.10.0/24 and mail.companyA.com. While the penetration testing company was in the information gathering phase, it was discovered that the mail.companyA.com IP address resolved to 20.15.1.2 and belonged to Company B. Which of the following would be the BEST solution to conduct penetration testing against mail.companyA.com?
Which of the following types of intrusion techniques is the use of an “under-the-door tool” during a physical
security assessment an example of?
A penetration tester is attempting to scan a legacy web application using the scanner's default scan settings. The scans continually result in the application becoming unresponsive. Which of the following can help to alleviate this issue?
An internal network penetration test is conducted against a network that is protected by an unknown NAC system In an effort to bypass the NAC restrictions the penetration tester spoofs the MAC address and hostname of an authorized system Which of the following devices if impersonated would be MOST likely to provide the tester with network access?
A penetration tester discovers Heartbleed vulnerabilities in a target network Which of the following impacts would be a result of exploiting this vulnerability?
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing
application. Which of the following would be the BEST remediation strategy?
During post-exploitation, a tester identifies that only system binaries will pass an egress filter and store a file with the following command:
c: \creditcards.db>c:\winit\system32\calc.exe:creditcards.db
Which of the following file system vulnerabilities does this command take advantage of?
A penetration testing company is performing a penetration test against Company A. Company A has provided the IP address range 10.0.0.0/24 as its in-scope network range. During the information gathering phase, the penetration tester is asked to conduct active information-gathering techniques. Which of the following is the BEST tool to use for active information gathering?
A penetration tester has gained access to a marketing employee's device. The penetration tester wants to
ensure that if the access is discovered, control of the device can be regained. Which of the following actions
should the penetration tester use to maintain persistence to the device? (Select TWO.)
A penetration tester must assess a web service. Which of the following should the tester request during the scoping phase?
Given the following Python script:
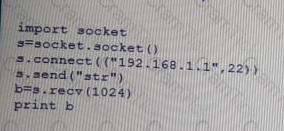
Which of the following actions will it perform?
An Internet-accessible database server was found with the following ports open: 22, 53, 110, 1433, and 3389. Which of the following would be the BEST hardening technique to secure the server?
Which of the following CPU register does the penetration tester need to overwrite in order to exploit a simple butter overflow?
Which of the following BEST explains why it is important to maintain confidentiality of any identified findings when performing a penetration test?
A penetration tester is asked to scope an external engagement. Which of the following would be a valid target?
A senior employee received a suspicious email from another executive requesting an urgent wire transfer.
Which of the following types of attacks is likely occurring?
A penetration tester is performing a code review. Which of the following testing techniques is being performed?
A penetration tester attempts to perform a UDP port scan against a remote target using an Nmap tool installed onto a non-Kali Linux image. For some reason, the UDP scan falls to start. Which of the following would MOST likely help to resolve the issue?
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon discovering vulnerabilities, the company asked the consultant to perform the following tasks:
Which of the following has occurred in this situation?
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
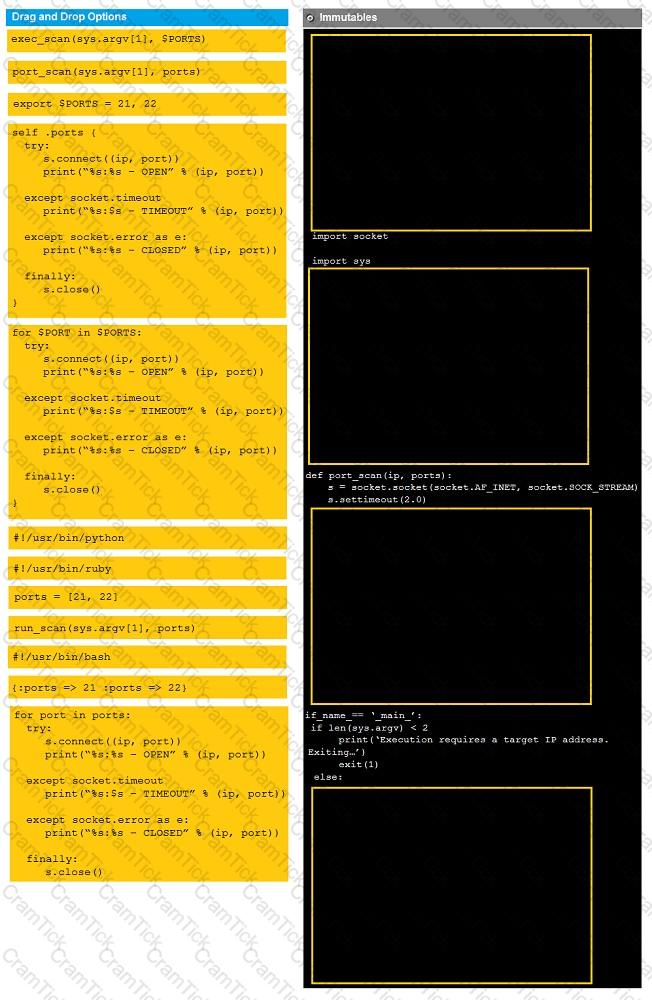
A penetration tester is scoping an engagement with a company that provided a list of firewall rules and a digital network diagram. Which of the following tests would require this data?
A penetration tester is able to move laterally throughout a domain with minimal roadblocks after compromising
a single workstation. Which of the following mitigation strategies would be BEST to recommend in the report?
(Select THREE).
During a penetration test a tester Identifies traditional antivirus running on the exploited server. Which of the following techniques would BEST ensure persistence in a post-exploitation phase?
A penetration tester is testing a banking application and uncovers a vulnerability. The tester is logged in as a non-privileged user who should have no access to any data. Given the data below from the web interception proxy
Request
POST /Bank/Tax/RTSdocuments/ HTTP 1.1
Host: test.com
Accept: text/html; application/xhtml+xml
Referrer: https://www.test.com/Bank/Tax/RTSdocuments/
Cookie: PHPSESSIONID: ;
Content-Type: application/form-data;
Response
403 Forbidden
Displaying 1-10 of 105 records
Which of the following types of vulnerabilities is being exploited?
After successfully capturing administrator credentials to a remote Windows machine, a penetration tester attempts to access the system using PSExec but is denied permission. Which of the following shares must be accessible for a successful PSExec connection?
Which of the following describe a susceptibility present in Android-based commercial mobile devices when organizations are not employing MDM services? (Choose two.)
If a security consultant comes across a password hash that resembles the following
b117 525b3454 7Oc29ca3dBaeOb556ba8
Which of the following formats is the correct hash type?
When conducting reconnaissance against a target, which of the following should be used to avoid directory communicating with the target?
During the information gathering phase, a penetration tester discovers a spreadsheet that contains a domain administrator's credentials. In addition, port scanning reveals that TCP port 445 was open on multiple hosts. Which of the following methods would BEST leverage this information?
When calculating the sales price of a penetration test to a client, which of the following is the MOST important aspect to understand?
In which of the following scenarios would a tester perform a Kerberoasting attack?
A security consultant is trying to attack a device with a previously identified user account.
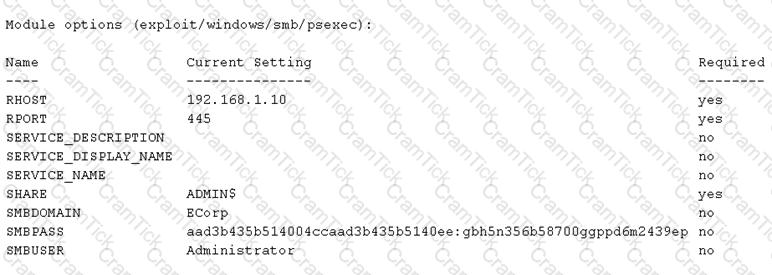
Which of the following types of attacks is being executed?
A system security engineer is preparing to conduct a security assessment of some new applications. The applications were provided to the engineer as a set that contains only JAR files. Which of the following would be the MOST detailed method to gather information on the inner working of these applications?
Which of the following is the BEST way to deploy vulnerability scanners with many networks segmented by firewalls with active IPS rules?
A security assessor is attempting to craft specialized XML files to test the security of the parsing functions
during ingest into a Windows application. Before beginning to test the application, which of the following should
the assessor request from the organization?
During a penetration test, a tester runs a phishing campaign and receives a shell from an internal PC running Windows 10 OS. The tester wants to perform credential harvesting with Mimikatz.
Which of the following registry changes would allow for credential caching in memory?
A penetration tester has compromised a system and wishes to connect to a port on it from the attacking machine to control the system Which of the following commands should the tester run on the compromised system?
PenTest+ | PT0-001 Questions Answers | PT0-001 Test Prep | CompTIA PenTest+ Exam Questions PDF | PT0-001 Online Exam | PT0-001 Practice Test | PT0-001 PDF | PT0-001 Test Questions | PT0-001 Study Material | PT0-001 Exam Preparation | PT0-001 Valid Dumps | PT0-001 Real Questions | PenTest+ PT0-001 Exam Questions